 For convenience and security, instead of a password to open an encrypted disk, you can use electronic USB access keys. As a key, you can use a USB flash disk, a token, or a smart card. A full list of compatible devices can be found here.
For convenience and security, instead of a password to open an encrypted disk, you can use electronic USB access keys. As a key, you can use a USB flash disk, a token, or a smart card. A full list of compatible devices can be found here.
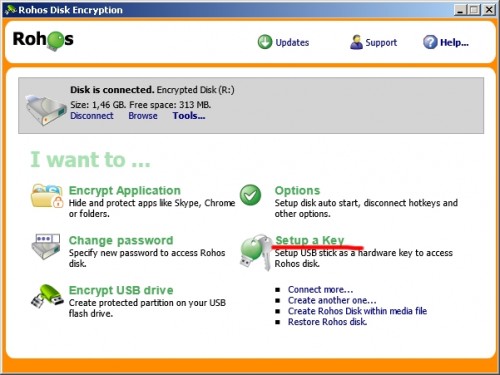
The master user can set a key for a disk immediately after installing the program, or by using the command Setup a Key in the main program window (see picture).
The password for the disk will remain on the key in encrypted form. When using some tokens users must also set and remember a PIN. All devices, except USB flash disks, require you to first install the manufacturer’s drivers. Some tokens or smart cards must first be initialized with the manufacturer’s utility. In our blog, you will find an overview of the most popular devices for protecting your information.
Of course, for an encrypted disk placed on a USB storage drive, you cannot use this same USB device as an access key.
Open the program options. Here it is possible to configure automatic activation of an encrypted disk when the key is connected, as well as automatic disabling of the disk when the key device is removed.
Tips for using an electronic key for securing information
Electronic keys have now proven to be useful and essential tools for many years. This is a durable and reliable means of securing information. Below we will give some tips that we think are especially important:
- A spare copy of the key significantly eases access to your information in the event that your key is lost or damaged. If you have decided to use an electronic key, then buy two, configure them both, and keep the second key as a backup.
- If you decide not to create a second key, then a good solution is to create a backup copy of the certificates and other important information on the key. This is also a good practice in general. Such backup copies should be kept in a secure place.
- If you are the owner of a notebook computer, then use a micro-version of the key. They do not stick out much from the notebook and aren’t so prone to damage. See our overview of ruToken micro keys.
- It is important to note that you don’t have to worry about leaving the token connected to the notebook or computer while you are away from it. Thanks to the use of a PIN, the electronic key itself is always kept safe from a third party. No one can use the key without the PIN, and entering a PIN incorrectly three times will block the key. Unblocking a key can be done with an Administrator’s PIN.
- By default, the Administrator PIN is set on all tokens and its default value is set out in the documentation. For that reason, its value must be changed. You can only change an Administrator PIN using the utility for tokens, which is provided by the manufacturer. We again recommend that you keep your new Administrator PIN in a safe place.
In the Rohos Disk program, there is a convenient function to block access to a Rohos disk when you are away. When you come back, the Rohos program will ask for the PIN for the token. You will have 25 seconds to answer before the disk is automatically disabled for security.
The screenshots: