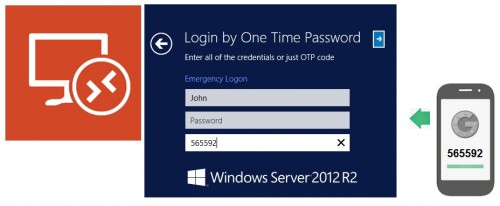
Rohos Logon Key provides secure 2-factor authentication for Windows Remote Desktop by using Mobile Phone or One-Time-Password tokens.
2-factor authentication intelligence:
- By using a smartphone with Google Authenticator application;
- When One-Time-Password is delivered to any mobile phone by SMS or Email;
- Allows to integrate 3rd party OTP code delivery service or devices like GSM modems;
- By using a hardware OTP generator like Yubikey/SecureID/SafeNet/Feitian;
- Each user account can be configured with any type of 2-factor authentication means Google Auth / SMS or Email delivery or security devices like PKCS#11 tokens.
The benefits of 2-factor authentication for Remote Desktop:
- User must provide new OTP code each time for login;
- Each generated OTP code is unique and cannot be duplicated by the user;
- Allows to restrict Remote Desktop access by user list or user group;
- You don’t need to install Rohos on a client PC/device you log in from;
- 2-factor authentication applied by the List of users / Active Directory group membership or IP address filter;
- Review and include 2FA audit log into any existing SIEM;
Rohos Logon Key allows accessing Windows Remote Desktop in a secure way by using the popular and secure One-Time-Password authentication technology replacing weak password-based login.
- How it works
- Installing Rohos Logon Key on Terminal Server
- How to enable 2-factor authentication for a user account
- How to register multiple users with Google Authenticator
- Using automated 2-factor authentication by sending OTP code by SMS
- How to disable or reset 2-FA for the user account
- Registering multiple 2FA users with OTP configuration in an automated way
- Enabling 2-FA by using client IP filter
- Licensing Rohos Logon Key
How it works
Rohos Logon Key integrates or replaces Windows Terminal Services, authentication provider. It works by adding a two-factor authentication level to the existing authentication infrastructure. After deployment users can log into remote session only by using 2-factor authentication: OTP code and regular login data.
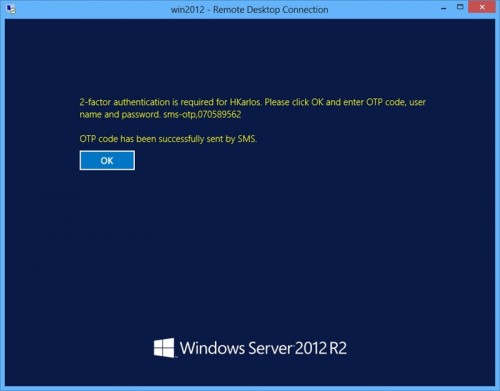
Rohos Logon Key message requiring 2-factor authentication :
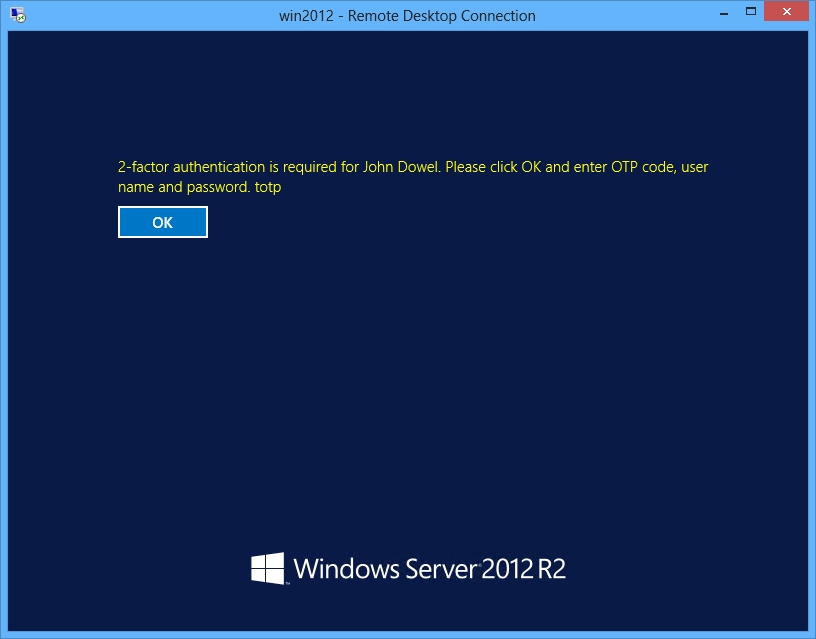
A user is entering an OTP code to continue login into Remote Desktop :
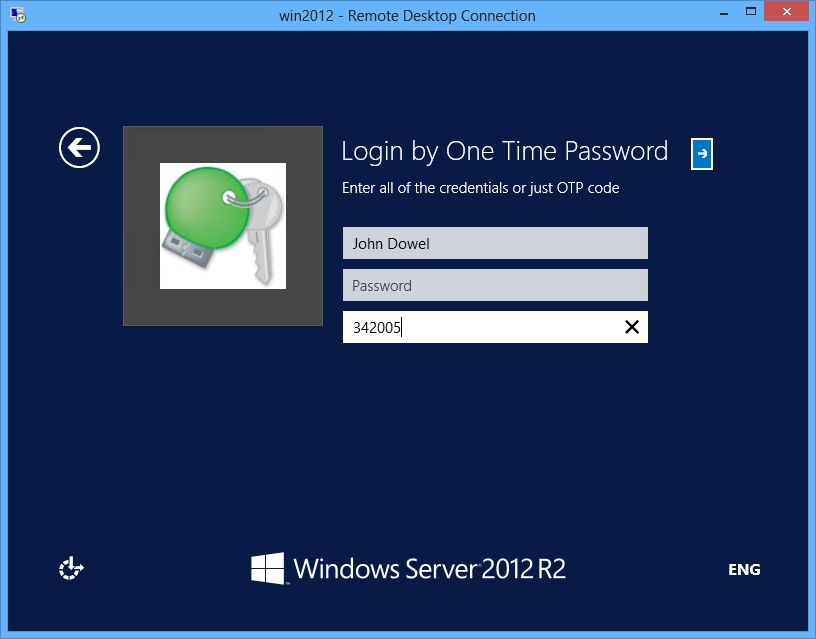
Or when using web-based access for Remote Applications (RDWeb) you just need to click the “Show Details” button and enter an OTP code to start using an application.
Read next to find out how to configure it.
Installing Rohos Logon Key on Terminal Server
1. Install Rohos Logon Key on the Windows 2008/2012 Terminal Server :
Download 15-day trial Rohos Logon Key.
2. Choose a 2-factor authentication policy:
- For all users
Any user account will be required to pass 2FA.
- For listed users
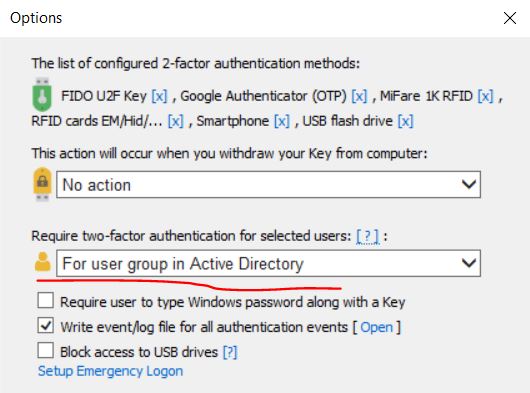
Only configured users will be required to use 2-factor authentication for login. Any other users will be able to login by a password as usual. The user list is created automatically by the “Setup a Key” dialog box. To review the list open the “Users and Key” dialog box. - For 2FA user group in Active Directory
Each user from a specially designated user AD group (default name is ‘Rohos’) will be forced to pass 2-factor authentication during Remote Desktop login.
Please note: ‘rohos’ user group should be created by an Active Directory Administrator ; - For Remote Desktop login
All Remote Desktop sessions will be required to pass 2-factor authentication; You can set the IP filter to specify LAN addresses that need to bypass 2FA. Only users, who came through the dial-up, DSL connection, and from other networks, will be required to pass 2-factor authentication. - For Remote desktop users from the 2FA AD group
Only users, who came through outside networks and belongs to the 2FA group will be required to pass 2-factor authentication.
You should have Windows 2008 R2/ 2012 / 2016 Server as your Terminal Server to try it.
4. Setup Emergency Login
In order to prevent Terminal Server login lockout due to the 2-factor authentication policy, we recommend to set up the Emergency Login option. This will allows the Administrator to login into the Terminal Server console/remote desktop by using: UserName, Q&A entry, and password. Emergency Login does not require 2-factor authentication. Emergency Login is not required if you have Server Console access possibility.
How to set up a user account for 2-factor authentication
2-factor authentication is applied individually for each user account. Automated setup is possible only by using the “OTP delivery by SMS” option.
In order to set up a 2-factor authentication for a user account open Rohos Logon Key > Setup OTP Token:
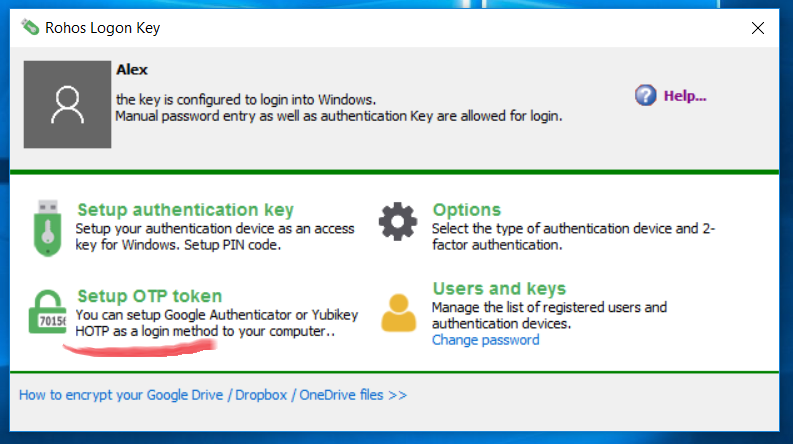
Setup One Time Password authentication dialog box:
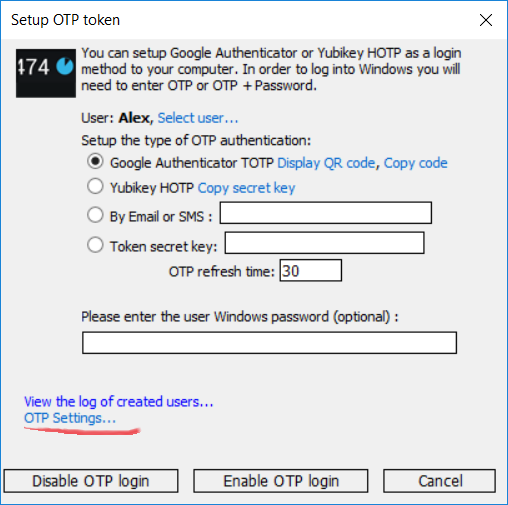
- Select the user account;
- Choose the type of One-Time-Password generator that user will use;
- Leave a password field blank
- Click “Enable OTP login” to apply the configuration.
Click “Display QR-Code” and “Copy code” to configure Google Authenticator or send Google Authenticator configuration by email to the user.
When using the “OTP by Email/SMS” option:
– Enter mobile phone or ensure there is a mobile phone field in AD User Account properties is filled in.
– Or enter user email;
– Ensure to properly set up the OTP delivery method by clicking on OTP Settings… link.
How to register multiple users with Google Authenticator
Rohos Management Tools provides a secure and scriptable way to set up multiple users with Google Authenticator 2FA and deliver 2FA configuration by email or SMS.
Rohos Management Tools allows to :
– Configure a group of users with Google Authenticator 2FA;
– Deliver Google Authenticator configuration to the user by Email;
– Setup a custom delivery method like SMS / Text File / Webserver publishing.
– Resend, Reset or Delete OTP configuration for the already registered 2FA users.
Enabling automated 2-factor authentication by SMS / Email
Rohos Logon Key allows using automated 2-factor authentication for Remote Desktop users. Rohos will automatically create a 2FA configuration and sent One-Time-Password code by SMS to the user account’s mobile phone number or email during each login into Remote Desktop.
Your Terminal Server must meet the following requirements:
- User account fields: telephone/mobile number Or email; must be filled in;
- Rohos Logon Key is configured with SMS-gateway support Or Email credentials in OtpDeliveryScript.ps1;
Setting-up Automated OTP configuration:
First, we recommend to test OTP deployment on a small user group:
- Open Rohos Logon Key > Settings and set “For user group in AD” 2FA policy.
- Create an AD group named “Rohos” and add a few user accounts that will be used to test automated 2FA deployment.
- Try to login with these user’s accounts via RDP.
– Rohos will automatically create an OTP config and send OTP by SMS or PS Script.
– check OTP delivery status and make a test OTP delivery by opening Setup OTP > Otp Options. Choose a user and click “Test Delivery”.
When your test is successful you can change the 2FA policy to “Remote Desktop users” or add more users to the AD 2FA group (Rohos).
Setting up SMS-gateway as OTP-delivery method:
Requirements:
- An account in 3rd party SMS gateway \ delivery service with HTTP API to send SMS messages.
Open Rohos Logon Key > Setup OTP Token > OTP Settings…

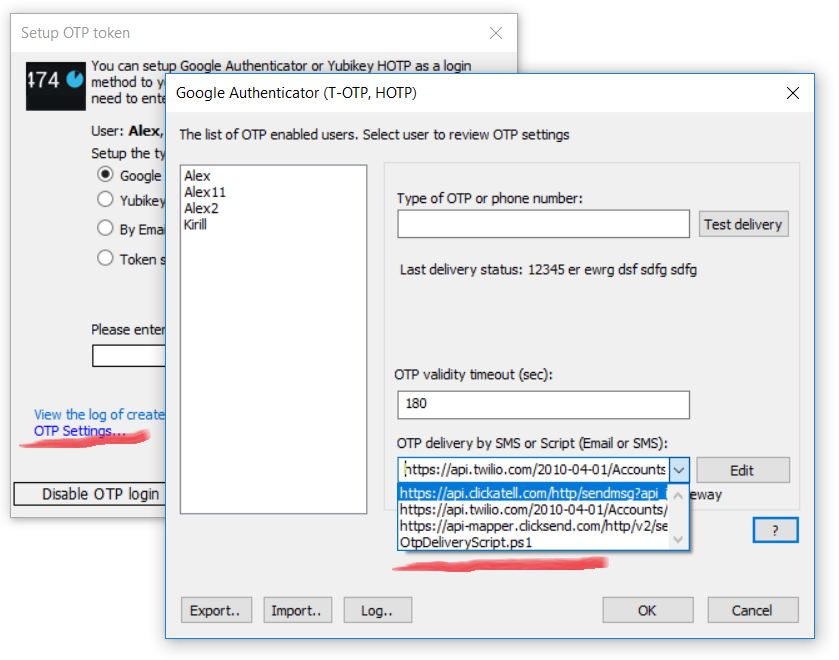
Select predefined HTTP service API or enter another HTTP API URL, for example:
https://api.clickatell.com/http/sendmsg?api_id=xxxx&user=xxxx&password=xxxx&to=%phone%&text=%text%
where %phone% %text% variables will be replaced with the phone number of the user and the actual OTP code as a text message.
Setting up Email based OTP delivery authentication
It is also possible to combine SMS with the Email method to deliver OTP code for authentication. To archive this flexibility you need to choose “OtpDeliveryScript.ps1” option.
Requirements:
- PowerShell v.3 and higher (Windows 2012 R2 and higher has it by default);
Or Windows 2008 with an update; - The script execution policy is enabled;
In order to enable it to run the “Set-ExecutionPolicy -ExecutionPolicy RemoteSigned” command in PowerShell ISE (x86). You need to run both “PowerShell” and “PowerShell (x86)” as Admin and execute this command; See the screenshot.
Click Edit to open OtpDeliveryScript.ps1 file and edit Email options such as SMTP server, email and password credentials for the mailbox that will be used to send emails:
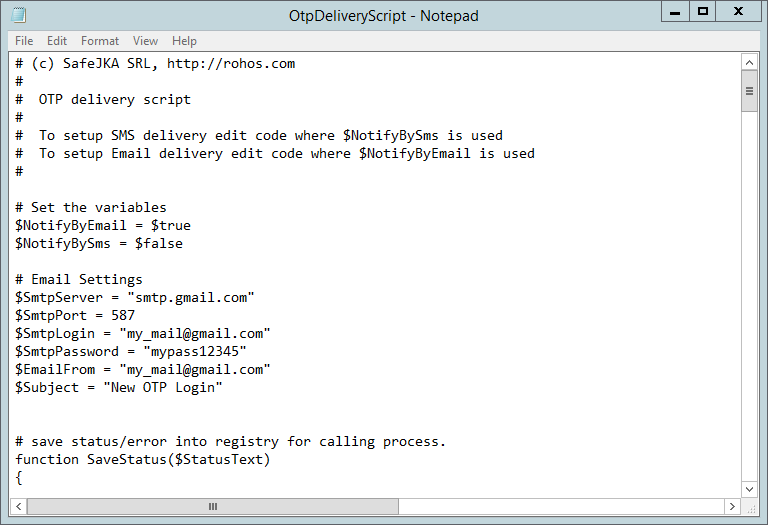
To setup SMS delivery Find string:
$SmsGatewayUrl = “https://api.clickatell.com/http/sendmsg?api_id=xxxx&user=xxxx&password=xxxx&to=$($AdUserName.telephoneNumber)&text=$($SmsNotificationText)”
And customize xxxx URL parameters so that it should be your SMS provider HTTP API URL;
Both $($AdUserName.telephoneNumber) and $($AdUserName.telephoneNumber) are script variables and you should not touch them;
Here is an example of well-known SMS delivery services:
$SmsGatewayUrl = “https://api.clickatell.com/http/sendmsg?api_id=xxxx&user=xxxx&password=xxxx&to=$($AdUserName.telephoneNumber)&text=$($SmsNotificationText)”
$SmsGatewayUrl = “https://api-mapper.clicksend.com/http/v2/send.php?method=http&username=xxxx&key=xxxx&to=$($AdUserName.mobile)&message=$($SmsNotificationText)”
You may select a user from Left or enter Email/Phone and click the “test delivery” button to sent OTP code by using the configured delivery method. Please note: In order to use Gmail as an email delivery service you need to set up your Gmail settings: “Allow less secure apps”
https://support.google.com/accounts/answer/6010255?hl=en
Learn More about setting up an OTP delivery method by Email>
Remote Desktop login with SMS authentication enabled:
How to disable or reset 2-factor authentication
There are few ways to disable or reset 2-factor authentication for the entire Server or selected User account.
To disable the 2-factor authentication policy:
- Uninstalling Rohos Logon Key will restore default password-based or pass-thought authentication.
- Setting to “none” option of “Allows to login by USB key” will temporarily disable the 2-factor authentication requirement for all users.
To reset/change or disable 2-factor authentication for a user account:
- Removing user account from Rohos AD group may disable 2-factor authentication requirement for the user (just in case of policy “require 2-FA for Rohos group”)
- Open Rohos > Setup a Key dialog box > choose user account > and click disable OTP login. This will reset the 2-FA configuration for the user. OTP generator used by the user (Google Authenticator, Yubikey) will become invalid.
- Open Rohos > User and Keys dialog box > find the user and delete it from the list. This will disable the 2-factor authentication requirement for the user (just in case of policy “require 2-FA for the List of users”)
Registering multiple 2FA users with OTP configuration in an automated way
Rohos provides an automated way to set up multiple users with Google Authenticator. The enrollment QR-code will be delivered securely via email or SMS right to the user’s smartphone.
Control 2FA by using an IP filter
Rohos Logon Key allows to filter Remote Desktop connections by client IP address and require 2FA by IP mask.
How to try 2FA for Remote Desktop by using IP filter:
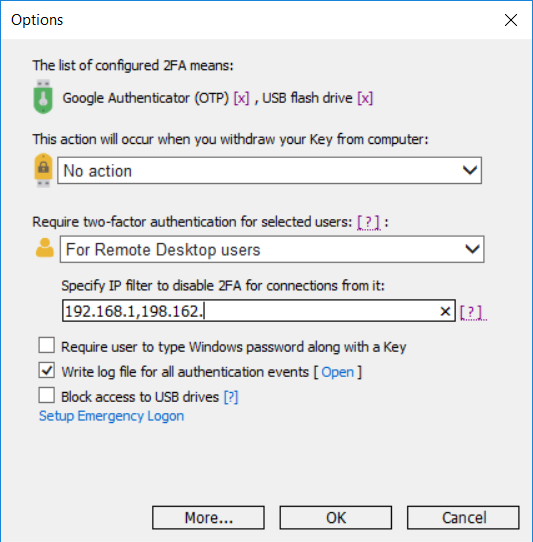
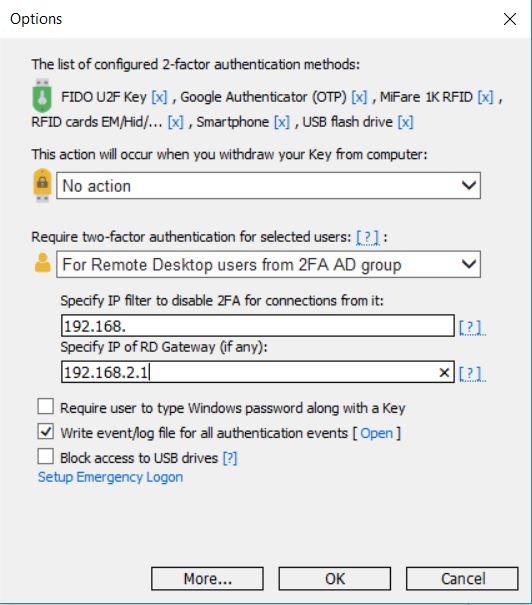
- In a Remote Desktop session open Rohos Logon Key > Options.
- Set option “Require two-factor authentication ..” to “For Remote Desktop users”.
- By clicking on [?] you can check if Rohos was able to identify your client’s WAN IP address.
- Specify “LAN IP Filter:”, this should be a prefix of your local LAN. By using this prefix Rohos will be able to differentiate between LAN and WAN connections and require 2-factor authentication for clients with WAN IP.
Licensing Rohos Logon Key
- Rohos Logon Key Server license is required for each Terminal Server host with Rohos Logon Key; Allows to protect unlimited users and have unlimited authentication keys;
- Rohos Logon Key Small Server license allows to protect up to 15 users;
Please note authentication by SMS requires 3rd party SMS gateway service that is not included in Rohos Logon Key and should be configured and paid separately.