 Summary: If you are the only holder of a computer or owner of a shared family PC – you might still want to set up your computer with user accounts, privileges and other security rules and software. Doing so prevents unauthorized access to the Windows computer, makes it more stable and gives you joy sharing the home computer or surfing the Web online.
Summary: If you are the only holder of a computer or owner of a shared family PC – you might still want to set up your computer with user accounts, privileges and other security rules and software. Doing so prevents unauthorized access to the Windows computer, makes it more stable and gives you joy sharing the home computer or surfing the Web online.
Remember that even the higher computer security can be broken due to certain factors that you’ve missed. Check-out your system with the following list of security measures.
List of Measures
- Disable computer boot from CD-ROM and floppy
- Password protects the BIOS
- Use encryption
- Avoid unknown applications (emails’ attachments)
- Use different passwords
- Use two-factor authentication
- Top 10 Tips
Disable computer boot from CD-ROM and floppy
- (CD/DVD-ROM, floppy, flash drives) The data security of your computer can be easily broken by the aid of bootable CD-ROM. This simple trick allows intruders to do the following: Get full access to your disk drive and all the files on it without the need of logging in.
- Reset the administrator password to a blank one.
- Steal your email correspondence stored in Outlook.
- Install a Trojan or virus program.
If one can boot from CD-ROM, your files can be accessed in your absence. You should disable all the boot devices except the primary hard disk HDD-0 (see picture below).
Here’s how to disable system boot from Floppy/CD-ROM:
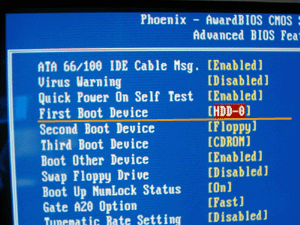
[Phoenix BIOS screen-shot that shows how to set up boot options for computer. Via CD-ROM or Floppy]
First, boot device should be always your primary Hard Drive Disk. (The second can be any other, but we recommend none)
Password protects the BIOS
All computers have the option to set up a password for entering BIOS. This allows to protect from changing First boot device’ option in the BIOS. BIOS also has some important settings that are:
- Option to require password to turn-on computer
- Computer date and time
- Protection of first boot sector of the Hard Disk Drive
- Wake-up-on-LAN option that allows to remotely turn-on your computer
How to set BIOS password:
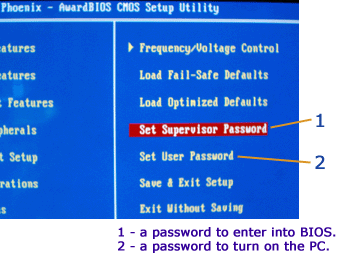
BIOS screen that allows to protect BIOS and changing bootable options.
How to set a password to BIOS to protect from changing the vital system options (first boot device, access password, etc.).
Use encryption
Use disk encryption to enhance your privacy.
For safe and 100% data protection we recommend to use data encryption software. Why? Learn here
Avoid unknown applications
Don’t open or execute files you are not sure by 100% of, no matter where or how you get them (email attachments, etc.).
- Get a good antivirus program: NOD32 or Norton Antivirus and keep it updated!
- Get spyware cleaner program.
Some unfair (XXX) websites use the security defects (bugs and ‘holes’) of the popular operating systems (web browsers) in order to install malicious programs and modules on any computers, without any permission.
Use different passwords
The same password is a common mistake most of us commit.
Imagine the following situation: you have 2 email accounts, an ICQ account, one computer at home, one in the office, and a handheld device. All of them are protected with the same password.
Imagine that certain circumstances forced you to connect to ICQ from a computer in an Internet café. Public terminals are beyond your control, hence you are unable to assure that there is no spyware running on them, or that all the security measures were taken. In this case, your ICQ password is likely to be recorded somewhere.
If that happens, then all your accounts\computers have become unprotected, even if you follow the guidelines mentioned in this manual.
This threat could have been minimized if you used different passwords.
In case your memory is not your strongest point, we have the solution – multi-factor authentication. You can store your passwords on a USB flash drive, use password hint or PIN code.
Use two-factor authentication through USB stick
This is secure, reliable and cost-effective way to log in into Windows and access your private files. Tesline-Service SRL has developed a convenient solution for replacing your Windows password with a USB flash drive.
The idea behind two-factor authentication is that more than one factor (password) is required for the authentication to succeed.
For instance, Rohos Logon Key can enhance a password prompt with the requirement to plug in a USB flash disk (or USB stick, pen drive) into the computer.
One-click USB key setup and your regular USB flash drive is ready for secure Windows login.
Tips
– How to choose a correct password? Which guidelines should I follow when creating a password?
- The password should be not shorter than 7 characters
- It should be random, without any meaning
- Use UPPER case and lower case letters in your password
- Use special characters like these: _,&,~,(,.
So the ideal password should be like: Usa24_JD
(legend: Usa-smth. you like, 24 – smb. age, JD-smth. abbreviature).
Strong but not for human?
A big lie of computer security is that security improves as password complexity increases. In reality, complex passwords that comply with the above list of “security-enhancing” principles lead to one outcome: Users write down their passwords. Security is better increased by designing for how people actually behave: – Use hardware USB key to access your Windows account and private files.
- Update/patch your software now and then
- Use firewall, like ZoneAlarm to control what goes in and out from your computer
- Check / adjust your Windows security settings so they are safe
- Don’t use public computers for anything you need to type in your logins, they usually have keyboard monitors that capture your passwords/keystrokes.
- Make backups and store them in a safe place (at least once per month). The easiest way to do a total-backup is to make an “Image” of your hard drive or partition and store it on safe location.
Links
- How to use disk encryption to protect your privacy. Sharing a computer with someone else means that others could see your private files, install games or software you didn’t want, or change your computer settings. Learn the most appropriate ways to protect your sensitive information.
- Virtual encrypted disk inside-out. Rohos software creates a virtual encrypted disk within a file and mounts it as a real disk drive. Encryption is automatic, real-time (on-the-fly) and transparent.
Software Links
Rohos Logon Key – Smartest, most feature-rich USB security Windows login solution. Two-factor authentication via USB stick for fast login.
Rohos Disk – Smart disk encryption program. MS Office integration. Using two-factor authentication to access your files.
