BioSlimDisk biometric security token, Review, Comparison.
 Dear friends, recently we have covered “BioSlimDisk Signature” compatibility with some Rohos products. Now it’s time to review device security capabilities, compare it with other Biometric USB flash drives with fingerprint scanners and give you some hi-res photos of the device.
Dear friends, recently we have covered “BioSlimDisk Signature” compatibility with some Rohos products. Now it’s time to review device security capabilities, compare it with other Biometric USB flash drives with fingerprint scanners and give you some hi-res photos of the device.
In brief, BioSlimDisk is a USB flash drive with hardware level encryption (AES 256 bit key length) and hardware level Biometric authentication.
On the Manufacturer web site (RiTech Inc.) you may learn the features listed below with our comments:
- Protection using Biometric Area Sensor
Your fingers are the only authentication means to access the USB flash drive data. There is no backup password to access the device in emergency case. - 2 Admin and 4 User fingerprints
This is the obligatory configuration: Administrator should enroll (register) 2 fingers. Users should enroll 4 fingers. Without this enrollment the device is not working. And even more – these 2 or 4 fingers should NOT be the same fingers.
BioSlimDisk’s hardware-level Biometric Authentication module controls this enrollment and doesn’t allow using it without complete enrollment been done. - Dual-fingerprint authentication
In order to access the USB drive data user needs to enroll 2 fingers. This should be 2 different fingers from those 4 fingers that were enrolled by the user during setup. - Uses Dual authentication methodology
Again, the hardware level Biometric Authentication module is designed to authenticate user or admin by 2 fingers (from 2 or 4 fingers enrolled on setup). It requires user to touch biometric sensor by 2 fingers, one by one. If user fails to authenticate by one of the fingers 3 times in a row, the device power-off itself so you need to reconnect it to USB port. - Self-Destruct, Tamper protection and Chip-based Hardware AES 128 Encryption
The device self-destructs itself after 7 unsuccessful verifications and automatically turns off (i.e. 7 * 3 failed fingers). Also the chip itself has a tamper protection, i.e. when it detects a hardware protocol malfunction or intervention it destroys itself immediately. So in order to re-engineer the hardware you need to have a dozen of sticks for experiments. - True Driverless zero footprint technology (runs on all platforms e.g. Linux, Mac OS X, All Microsoft Windows, Solaris, etc.)
That is the almost amazing feature of this device. When you connect BioSlimDisk into USB port it gets the electrical power and turns-on the hardware-level Biometric Authentication module. After successful fingerprints authentication BioSlimDisk turns-on the USB flash drive with AES encryption. - Hardware level data encryption.
All data are encrypted/decrypted on-the-fly when you work with the token. AES key is generated after token Administrator enrollment.
The illustrations below show how it works and how it differs from other Secure USB flash drives with fingerprint authentication:
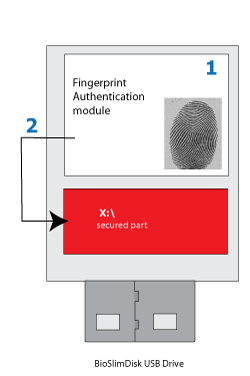
BioSlimDisk device authentication work-flow contains 2 steps:
On the picture:
- Only hardware-level Biometric Authentication module is activated upon plugging the device into USB port. It performs fingerprint authentication before goes to step 2.
- Biometric Authentication module turns on the USB flash drive. The device appears as a regular USB removable drive in computer.
The important part is that authentication is proceeded inside the device.
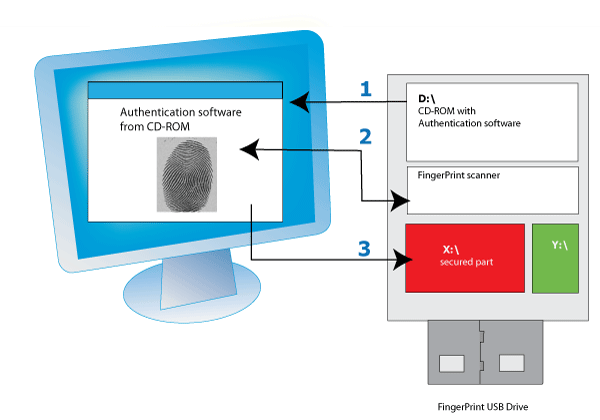
Let’s take a look at authentication work-flow of other USB flash drives equipped with biometric access control. Those that we have tested before: Apacer, Transcend JetFlash, TakeMS Scanline, Silicon Power:
There are 3 steps on the picture:
- Upon plugging the device into USB port the device turns-on Drive D:\ – CD-ROM drive with an authentication and enrollment software. And also it gives access to the Drive Y:\, this is an open-part of the entire drive (user defines this open-part during setup).
In order to access secure Drive X:\ user starts the Authentication software from D:\ - Authentication software uses a Fingerprint scanner from the device. The Software (or Hardware part) identifies fingerprints. Or there is a back-up password in case you don’t want to use fingers.
- The Authentication software (or Hardware depending on the model) makes a decision to turn-on the secured drive X:\.
As we see this authentication work-flow may have some vulnerabilities depending on the implementation:
- Software-level biometric authentication. It’s possible to sniff the USB-traffic and re-engineer security protocol to find security holes or issues that maybe used to access Secured Drive X:\ or change internal configuration of the device.
- It’s possible to recover a Back-up password by using a brute-force attack. As there are no attempts limit. And looks like hardware-part doesn’t control it.
After this comparison we see why BioSlimDisk doesn’t require drivers and is compatible with any OS – it doesn’t use any software-component. The second important thing is that internal configuration of the BioSlimDisk cannot be changed other way except the Authentication Module interface.
How strong Hardware Authentication could be?
From our experience with Biometric technology we know that it is not possible to use fingerprint or any other biometric material to generate AES encryption key and to use it then in encryption process. So it looks like encryption keys are stored somewhere on the BioSlimDisk chip. Therefore BioSlimDisk’s authentication hardware just compare biometric materials to make a decision to begin decryption process by using a stored AES key. This is not an ideal security protocol.
Depending on hardware implementation getting the AES key may be a trivial job for a smart hardware engineer. Then the flash drive chip could be connected to regular USB flash drive board and decrypted by software. But new generation of BioslimDisk uses a chip based tamper protection makes chip hacking harder.
Read here the interesting story about hardware level security system of the 1st generation BioSlimDisk and other devices.
BioSlimDisk Administration
The BioSlimDisk is designed to have an Administrator and Regular User. I should mention here again that the device Authentication module checks the configuration and forces to make all necessary enrollments before normal use.
In order to run BioSlimDisk in Administration mode you should use side switcher as shown on this picture (on the picture switcher is in user-mode):
BioSlimDisk has side switcher on its case that controls whether it’s a regular use or administration use (re-enrollment). In Administration use the device also requires biometric authentication and then allows to re-enroll user or admin.
Normal usage
In normal usage when you plug the device into USB port the small LED lights show the status.
Flashing blue indicator – the device waits for a valid fingers:
The green indicator flashed – the finger gets successfully authenticated, go on with the second finger:
after all 2 fingers authenticated successfully the LED lights are off and USB flash drive letter appears in Windows or Mac OS X.
You have only 3 attempts for each finger to be recognized successfully. If you make 7 failed attempts (with the device reconnection) the device can be blocked forever (all indicators are flashing).
On the photos you may have noticed how I place my finger –
- As I connected my BioSlimDisk right into my MacBook it’s very comfortable for me to place fingers as you see on photos – across the device.
- Manufacturer advise to use USB extension cable with the BioSlimDisk and put fingers along the device.
- In my tests I found that you may put fingers both ways, and even mix the way how you put the fingers (along or across).
- It’s very important to remember which fingers and which way were enrolled during setup. The fingerprint scanner uses plain logic and doesn’t rotate thumbnails in the memory before verification 🙂
In order to close access to the BioSlimDisk memory you need to unplug the device. Please note: even if you restart\sleep your PC or Mac the device may stay as authenticated/open.
Windows Seven reported data transfer speed as 2-15 mb/sec.
Resume:
We found BioSlimDisk very secure and comfortable USB flash drive. The dual-authentication principle enforces users to keep high level of security thus leaving no chances for bad guys. The Administration mode makes this device suitable even for small corporates that need protected portable storage with a central Administration features.
The regular users may enjoy the portable security offered by BioSlimDisk that doesn’t require administration privileges to be used on public PCs. The Admin/User feature may be reused here to share the device between family members.
The only-hardware authentication makes the device security unbreakable for regular software-based hackers, but depending on the hardware authentication module there maybe chip-based vulnerabilities.
Additional info: Comparison of USB flash drives with Encryption & Biometrics BioSlimDisk, IronKey, Kanguru, Kingston.
Photos