Using Google Authenticator OTP for Windows login
The access to your computer or user account is usually password-protected. But sometimes it is not enough, especially, when your data requires high level of confidentiality. You don’t want to provide attackers with the chance to get hold of your most secret stuff and your data, don’t you? We has included Google Authenticator and Yubikey HOTP support into Rohos Logon Key. Now Windows login is performed in High-Safety mode by using Time based One Time Password and HOTP codes.
If you have Android, iOS or BlackBerry phones, use Google Authenticator program. Protect your computer with strong OTP password (One Time Password). OTP password – is the password generated by special device or program, and it is valid only once and right at the moment it has been generated. And there is no sense to spy on or capture such password. Whenever you try to enter the same password one more time or a bit later i.e. beyond the time interval predetermined – it will be rejected. Each time you log on to your computer, you will be requested a new OTP password from your phone.
Integrated into Rohos Logon Key program, Google Authenticator will serve as logon key to your PC. You will always have your secret password with you in your phone. You won’t have to enter Windows password manually, the program will do it for you. Comfortable and reliable. OTP token can be used along with other types of key. So, you can configure both: OTP and Flash drive and use one you prefer in the moment.
How to use Google Authenticator app to log in to your PC?
So, let us take, for example, the Android phone and consider how to set up Rohos Logon Key for Windows using OTP password from Google Authenticator app.
1. Make sure you have Google Authenticator app intalled on your phone. (Googles or Barcode Scanner additionally may be required for QR code scan).
2. Once the applications installed on the phone, you can start setting up Rohos Logon Key for your computer.
- Install the latest Rohos Logon Key v3.4 for Windows.
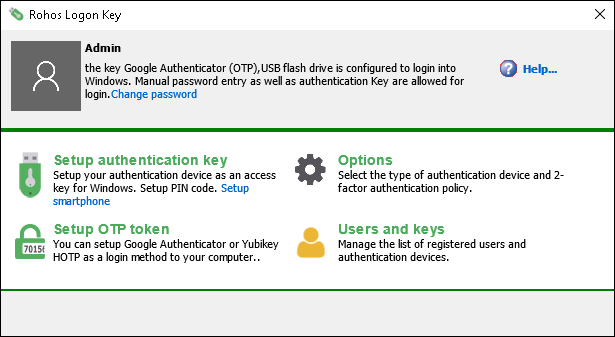
- Open Rohos Logon > Setup OTP token.
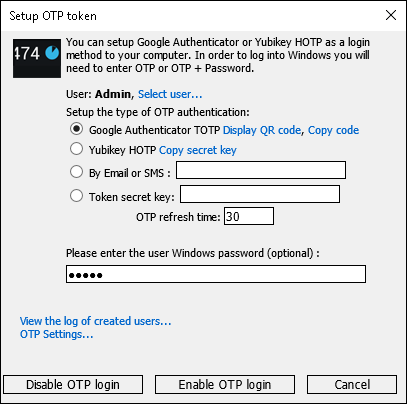
- Choose “Google Authenticator” and Click Display QR-code
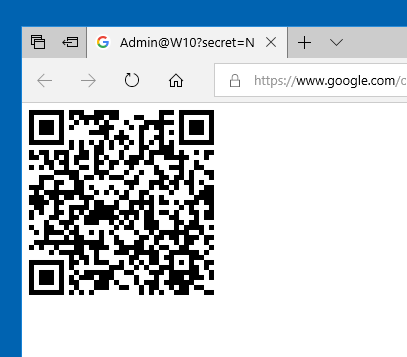
- Launch in your phone the Google Authenticator application and scan the barcode. Then hold your phone in front of the monitor for the barcode to be captured by the program.
- Optionally you may enter your current Windows password – if you want to replace your Windows login & pwd with only OTP code. This is less secure is some circumstances.
If you left password field blank – then you will need to use User Name + Password + OTP code for Windows login. - Click Enable OTP login button.
Done! From this moment your mobile phone works like access key for your Windows.
It means your mobile phone with Google Otp works like a digital key for windows login and desktop unlock as well
Google Authenticator will provide a computer name for each PC and register the name of Rohos Logon program. Thus, you can set up one phone and use it as a double protection key for any of your computers, be it your office computer, your personal notebook or any other PC you work with.
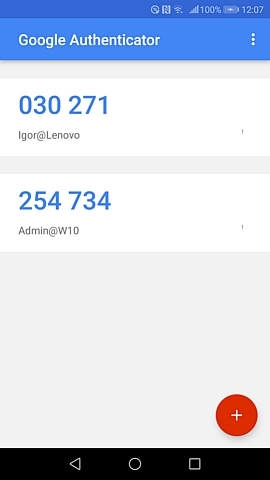
The smart phone screenshot shows that Google Authenticator application has been set up for logging in to two computers. To avoid any confusion the name of the computer will be given above each secret key. To the right of the one-time password there is a 30 second timer’s time for entering the password. Once the time interval has expired, a new password will be generated.
3. Enforcing strong 2-factor authentication
You may still login into Windows by using your Windows password as usually or by using Rohos Logon Key icon (by Google Authenticator OTP code).
If you wish to make your Windows authentication more secure you should enable 2-factor authentication in Rohos.
Open Rohos Logon Key > Options dialog and choose another value in the list «Require two-factor authentication for selected users». This will enforce 2-factor authentication for all or selected users.
And now in order to login they need to provide OTP + their Windows password. No one else will be able to login just by password.

4. If you have selected ‘for any user’ option please set up an ‘Emergency Logon’ option also in order to be able to access Windows in case your phone is not available.
We recommend that you use a two-factor authorization in Windows. In case of two-step authorization in the Windows authentication box you will be requested to enter both OTP one-time key and standard password for Windows. Two-factor authentication logon will provide you with double protection keeping curious and unwanted people away from your data. Or it can stop too smart and tech savvy children from touching your personal info.
Note: After setting up Google Authenticator authorization do not forget your phone at home. In case you don’t have your phone with you, you will be able to log in to your computer only through Emergency Logon of Rohos Logon Key. The OTP key will be requested even if your computer boot-up is performed in a safety mode. This prevents your computer from being hacked.
How to use Yubikey HOTP configuration for Windows Login
You need any Yubikey 2.0 with a free slot configuration and Yubikey Personalization Tool.
First you need to setup Rohos Logon Key:
Execute Options, select Google authenticator(OATH).
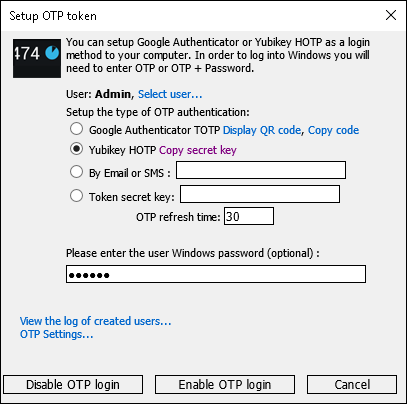
1. Open Rohos > Setup OTP token
If on your computer was previously installed Google Authenticator with Yubikey, click Disable OTP login.
2. Choose “Yubikey HOTP” and click “Copy secret key” – this will copy 20 bytes hex string into clipboard. It should be used later in Yubikey Personalization Tool.
3. Click Enable OTP login.
Now let’s setup Yubikey with HOTP configuration.
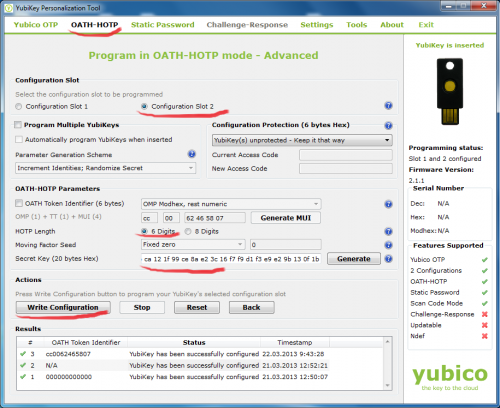
Setting up Yubikey second slot with HOTP by using Yubikey Personalization Tool
Insert Yubikey into PC and open Yubikey Personalization Tool:
- Click on “OATH – HOTP” > Advanced button
- Select free Configuration Slot. By default slot 2 is free.
- Ensure HOTP length is set to 6.
- Uncheck the option OATH token Identifier.
- Click on “Secret Key” field and paste (Ctrl+A and Ctrl+V) the secret key from clipboard (rohos copied it for you before).
If there were no 20 chars pasted – copy it again in Rohos Logon Key > Setup USB Key dialog box. - Click “Write Configuration”
Now your YubiKey 2nd slot is ready to be used for Windows Login. You need to restart your PC and Select Rohos Logon Key in welcome screen. Put your cursor in OTP field and long-touch your Yubikey.
Rohos Logon Key accepts both types of HOTP codes – with or without OATH identifier
cc0062465807101069 or
101069
last 6 digits are verified
Sending OTP codes by SMS/email to your mobile phone
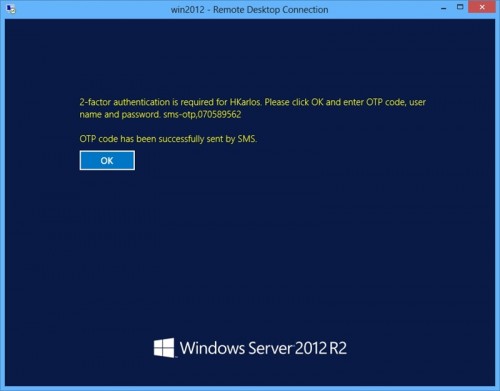
Rohos Logon Key allows to use automated 2-factor authentication for Remote Desktop users. Rohos will automatically sent One-Time-Password code by SMS to user account telephone number or email during login into Remote Desktop.
Your Terminal Server must meet the following requirement:
- Telephone/mobile number field contains user mobile number of the user; Or Email field is filled in;
- Rohos Logon Key is configured with SMS-gateway support or Email credentials;
Setting up SMS-gateway or another OTP-delivery method
Requirements:
- PowerShell v.3 and higher (Windows 2012 R2 and higher has it by default);
Or Windows 2008 with an update; - Script execution policy is enabled;
In order to enable it run “Set-ExecutionPolicy -ExecutionPolicy RemoteSigned” command in PowerShell ISE (x86). You need to run both PowerShell and PowerShell (x86) as Admin and execute this command; See the screenshot. - An account in 3rd party SMS gateway \ delivery service with HTTP API to send SMS messages.
Open Rohos Logon Key > Setup OTP Token > OTP Settings…
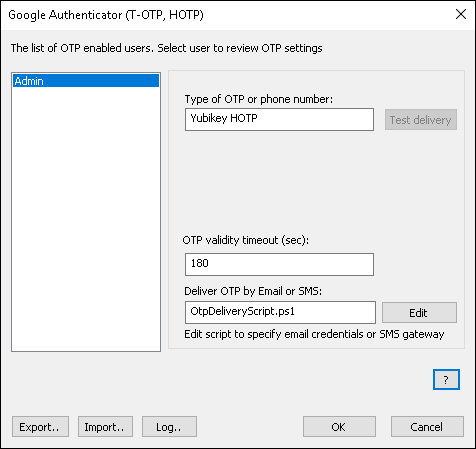
- Click Edit to open OtpDeliveryScript.ps1 file and edit Email options such as smtp server, email and password credentials for the mailbox that will be used to send emails:
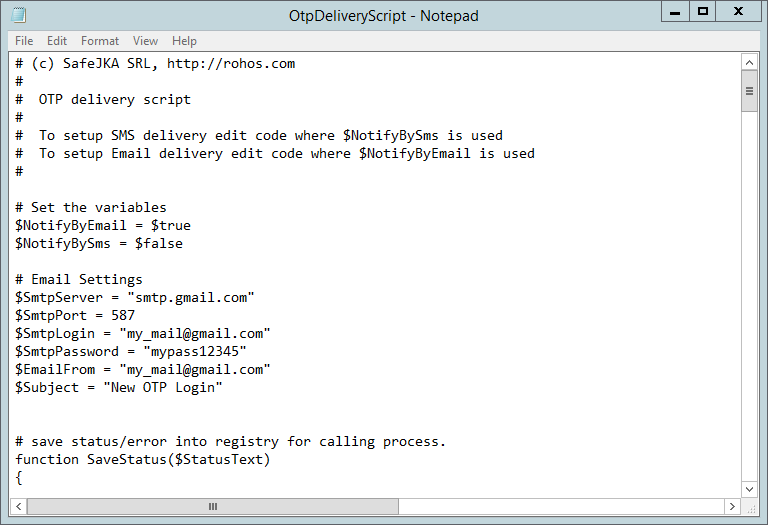
To setup SMS delivery Find string:
$SmsGatewayUrl = “https://api.clickatell.com/http/sendmsg?api_id=xxxx&user=xxxx&password=xxxx&to=$($AdUserName.telephoneNumber)&text=$($SmsNotificationText)”
And customize xxxx URL parameters so that it should be your SMS provider HTTP API url;
Both $($AdUserName.telephoneNumber) and $($AdUserName.telephoneNumber) are script variables and you should not touch them;
Here is an example for well known SMS delivery services:
$SmsGatewayUrl = “https://api.clickatell.com/http/sendmsg?api_id=xxxx&user=xxxx&password=xxxx&to=$($AdUserName.telephoneNumber)&text=$($SmsNotificationText)”
$SmsGatewayUrl = “https://api-mapper.clicksend.com/http/v2/send.php?method=http&username=xxxx&key=xxxx&to=$($AdUserName.mobile)&message=$($SmsNotificationText)”
You may select user from Left or enter Email/Phone and click “test delivery” button to sent OTP code by using configured delivery method. Please note: In order to use gmail as email delivery service you need to setup your gmail settings: “Allow less secure apps”
https://support.google.com/accounts/answer/6010255?hl=en
Learn More about setting up an OTP delivery method by Email>
Remote Desktop login with SMS authentication enabled:
Security benefits of using Google Authenticator for Windows Login
- Two-factor authentication – higher security level of Windows authentication:
Windows Password + Mobile phone is required for login. - No drivers or software are required for YubiKey or OTP by SMS.
- No USB port needed for Google Authenticator, it works without connection to computer.
- You may use Google Authenticator, YubiKey or just Mobile phone in the same time!
- Possibility for Network Administrator to login in a regular way by using just a password.
- Secure 2-factor login into Windows Remote Desktop with flexible authentication policy: by user list, group membership or only RDC users.
Rohos Logon Key Download
This update is free for all Rohos Logon Key registered users. But since April v.3.0 update will be paid.