The exceptionally small Rutoken Micro authentication device
Simply put, if you own a notebook and are concerned about the security of your information, then you should take a look at the micro version of this IT security key. Here you’ll learn about the Rutoken ECP Micro from Russia and the major advantages of its miniature design.

1. Miniature design
Just compare the full-sized Rutoken key device with this micro version. The full-sized version juts out from your notebook. The key is thus in a fragile position and can be easily brushed against and damaged. This is something you want to avoid, because you would waste time creating a new key from your backup copy. And if you don’t have a backup or spare copy of your Rutoken key at hand, how are you going to restore that backup?

2. Always on
Another important advantage of these micro tokens is that you don’t have to disconnect them from the notebook.
Why would you? A key feature of identifying devices like Rutoken is that they can protect themselves. You don’t have to worry about a Rutoken authentication device being stolen and you don’t have to always carry it on your keychain. No one except the owner can use a Rutoken without entering a PIN. Guessing a PIN is not possible since a malicious person only gets 3 tries to enter the correct PIN.
Only with a miniature USB identifier like Rutoken Micro can you:
— move the notebook from one place to another without unplugging the Rutoken from the USB port. You can put the notebook in a briefcase or open it anywhere without thinking about having to connect a Rutoken to access data or request authorization for your actions. The key is always where it has to be. This is a truly mobile solution.

Note: Keeping a backup of the data from the key and a backup Rutoken makes it significantly easier to replace the token in an emergency. If you are prepared for an event like loss or theft of your notebook, or damage to the token, then such accidents will not significantly affect your activities.
3. Securing data
Any identification device compatible with the PKCS#11 standard, like Rutoken, can be used to secure your data and access important resources.
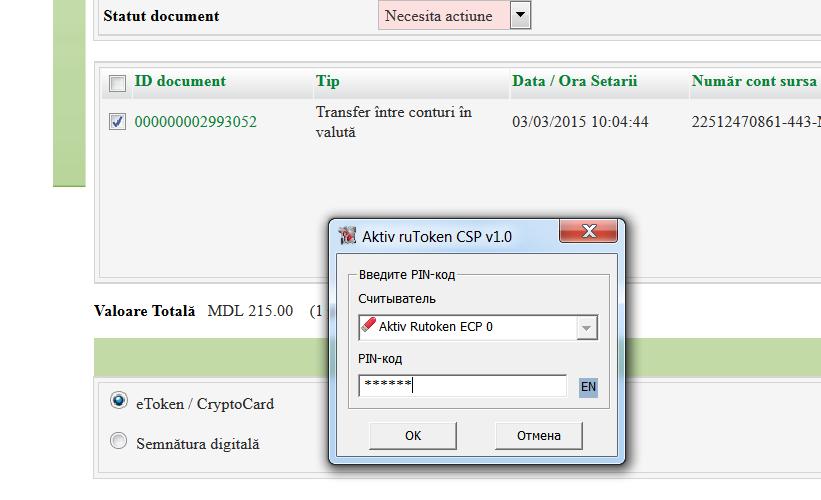
Internet banking with a digital certificate
All operations are protected with reliable two-factor authentication. Rutoken is able to store over 10 digital certificates at the same time.
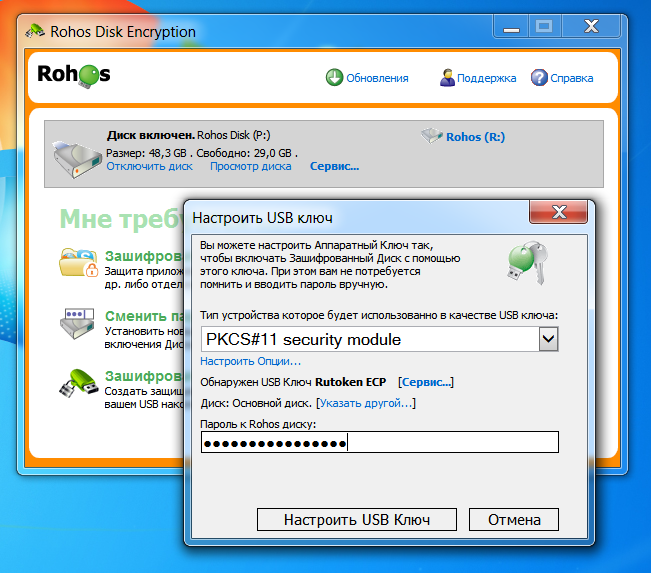
Encrypting a disk with Rohos Disk allows you to use a Rutoken as a key for accessing and decrypting the disk.
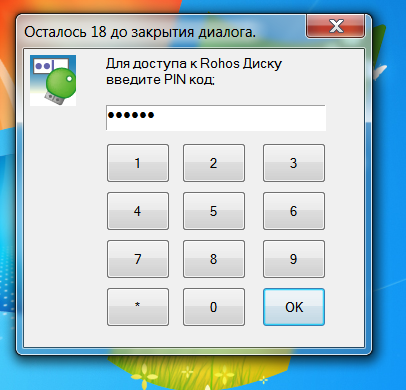
Confirm access to Rohos Disk when you open the notebook.
Rohos Disk will verify that a Rutoken has been connected and will ask for the PIN to ensure that you are the true owner of the key. If authorization is successful within 20 seconds after opening the notebook, you’ll be able to work with the Rohos Disk.
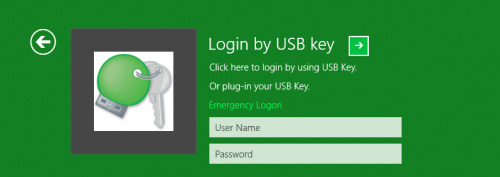
Constant data security on Windows:
The Rohos Logon Key program will verify that you are the owner of the notebook by means of a Rutoken and PIN. One Rutoken key can serve for accessing several Windows PCs, a terminal server, or a protected network resource.
Sample Rutokens for testing purposes are provided courtesy of the company Aktiv, Russia.
