Advise to setting up the admin account for OTP 2FA in conjunction with Rohos and remote access
We would like to share some advice regarding two-factor authentication and its use with an admin account when logging into Windows RDP. If it is not enabled currently we would strongly advise setting up the admin account for additional OTP authentication in conjunction with Remote Desktop access and Rohos Logon Key. Let’s review the pros and possible side effects.
Of course, it is highly recommended to use 2FA for the admin account, and it is definitely recommended rather than keeping it 1FA only. Just to remind you that default RDP login based on NLA credentials (user login and password in plain form store in .rdp connection file) from the client-side is quite vulnerable now since these credentials may be stolen and used by malware operators in an automated way – so the attack speed will be just 5-10 minutes. So today, the absence of additional authentication factors (2FA/MFA) is considered negligent. Even more, due to recent development in exploits and malware for Windows operating system, desktop sessions created by regular user accounts also may be elevated to Admin Privileges in Domain or Active Directory (AD) with a high success rate depending on your defense type (Anti-virus type, EDR solutions, etc). So a variety of exploits for horizontal/lateral movement in AD are huge also. But of course, Admin’s accounts are always a special target for cyber-criminals and traded as a high-price asset on the darknet.
To summarise, definitely you need to start your cyber-security efforts in 2FA from some point, and admin accounts are the right starting point, highlighting you have a cyber-security strategy. Especially with Rohos, since it is very easy to start with and has a fixed one-time price.
Regards to any side-effects of Rohos Logon 2FA. First, there is an “emergency logon” feature that helps to prevent accidental lock-out in case you lost your 2FA method (it may happen btw due to change of login habits). Rohos also has “2FA rules” that allow starting 2FA implementation by stages or user groups. Second, Rohos allows the introduction of new authentication methods in parallel or by user groups, depending on competence, budget, or platform requirements. We know that increasing security efforts requires time and adaptation by personal and technical resources. Combing these options with security awareness training with different user groups within the organization will be a good driver for cyber-security efforts to increase it in alignment with IT department maturity growth. And fixed, lifetime-pricing model of Rohos, allows focusing on cyber-defense rather than on budget logistics.
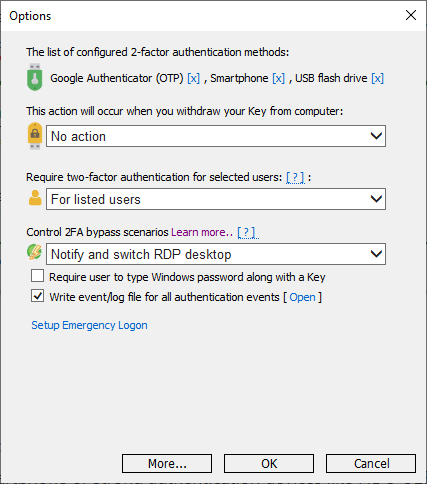
Recently we have added a new experimental feature that allows control over 2FA bypass or RDP session hijacking. It allows enriching cyber-security tactics by implementing certain “incident response” activities in regard to access controls. An immediate push notification will be delivered to the smartphone of the responsible person, and the session will be locked in case if Rohos detects the absence of 2FA means usage. In addition, Rohos access log file (access_log.txt) may be used as an additional event source in your SIEM system for this kind of event.
About Rohos Logon Key
Rohos Logon Key adds strong two-factor authentication control for Windows Remote Desktop access. Rohos allows to implement and adopt multi-factor authentication into business process with minimal side effects. You may combine different authentication methods: password, PIN code, Smartphone or strong authentication devices like FIDO U2F key, YubiKey, Google Authenticator One-Time password codes, SafeNet iKey tokens or RFID cards per different user groups depending on requirements or technical skills. With Rohos you can protect standalone computers, Active Directory workstations or Terminal Servers that work over RDP or other remote assistance solutions like TeamViewer or AnyDesk.
Download and try latest Rohos Logon Key v.4.8 (15-day trial) >>
Get your copy of Rohos Logon Key> (Server license is required to protect RDP access on Windows Server)
