Towards multi-factor authentication decision framework in Rohos Logon Key v4.0
We are glad to announce new Rohos Logon Key v4 for Windows. Now it has a possibility to combine two-factor authentication methods for a single desktop or user and define rules to support multi-factor authentication (MFA) control. Since 4.0 Rohos Logon Key will introduce rule-based multi-factor authentication decision support framework that brings MFA intelligence depending on access context. It automatically selects strong authentication method for privileged users or remote desktop access and convenient single-factor authentication when you use Windows computer in regular way on a desktop.
What’s new in brief:
- Multi-factor authentication decision support with possibility to use multiple 2FA modalities: Passwords, Yubikey security keys, FIDO U2F, RFID and Google Auth OTP for remote sessions; Rule-based access control intelligence;
- Twilio SMS gateway support for OTP based 2FA on Terminsal Servers;
- Two SMS delivery methods: by PowerShell script or by Rohos;
- Yubico v5 validation protocol and minor improvements on Microsoft Laptop;
- Added Amazon WorkSpaces and Azure VDI computers support. Simple and cost effective MFA for remote desktops with Google Auth OTP or Yubikey devices;
- Fixed issue with Display QR Code button.
- Added experimental feature to disable OTP history for multiple times usage . TOTP token can be used with a long period (5hr) and will be valid multiple times, but only inside its predefined time period of one day;
- Possibility to disable MFA for locked remote desktop sessions initially authenticated with MFA;
- Display regular user accounts on logon screen. Those users who are without 2FA control can be displayed on logon screen.
Options > More > Show users - Rohos Management Tools improvements. Import RFID Tags by CVS file. Edit Key by double click.
- Password replacement with RFID HID cards.
- Added support of OMNIKEY 5022 Smart Card Reader for MiFare 1K Cards.
- In Active Directory workstations Rohos writes 2FA events into Windows Event Log.
- Added support for Amazon WorkSpaces: MFA with Password + Yubikey or Google Auth OTP.
Rule-based multi-factor authentication intelligence
Rohos Logon Key includes the following rules to support dynamic MFA decision:
- By Active Directory group membership of the user of each access attempt;
- By IP address filtering of remote desktop user;
- By the criticality type of workstation;
We will continue expanding rule-based intelligence in future versions.
How to disable MFA for locked remote desktop sessions
When the remote screen is locked users have to enter a OTP key again to unlock. To increase user acceptance experience you can disable MFA during remote session unlock.
Currently this option is configured via Registry:
open regedit.exe and open :
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Rohos
create new DWORD value:
Disable2FA_on_RDP_unlock = 1
How to disable OTP history for multiple times usage
We have added “experimental feature” that allows to reuse OTP codes multiple time per a single day. If you are considering using “OTP” passwords to access offline computers, which are not connected to any kind of network. And you know the day and time the works begin, and it could take about a few hours. Then you can provide to computer operators a previously generated OTP codes (a small list of them for each day). So the OTP codes will have a validity for the selected work time and day.
Currently this option is configured via Registry.
Open regedit.exe and navigate to :
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Rohos
Create new DWORD value:
DisableOtpHistory = 1
Also increase a max possible OTP time interval ( Setup OTP > OTP settings > OTP validity timeout ) to 5 hrs (19000 sec)
Set longer timeout for Remote Desktop login session
When using an OTP via SMS/Email there maybe a longer delivery timeout. In this case Windows remote desktop services needs to be configured to keep remote login screen and allow user to wait and enter OTP code.
1. Goto: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\TerminalServer\WinStations\RDP-Tcp
2. Create DWORD
3. Name: LogonTimeout (DWORD)
4. Value: Specifies the time in seconds – Decimal Value – 300. Hex – (12c)its 5 minutes. – 3600. Hex (e10) is 1hr
https://serverfault.com/questions/422770/changing-the-login-timeout-for-windows-remote-desktop-services
MFA based on Goole Authenticator or SMS
Rohos Logon Key allows to combine Google Authenticator login method with OTP codes delivered by SMS each time you access remote desktop applications. In this improvement we added native support of popular SMS gateways such as twilio.
To use twilio you just need to select it from pre-defined methods and fix URL API string.
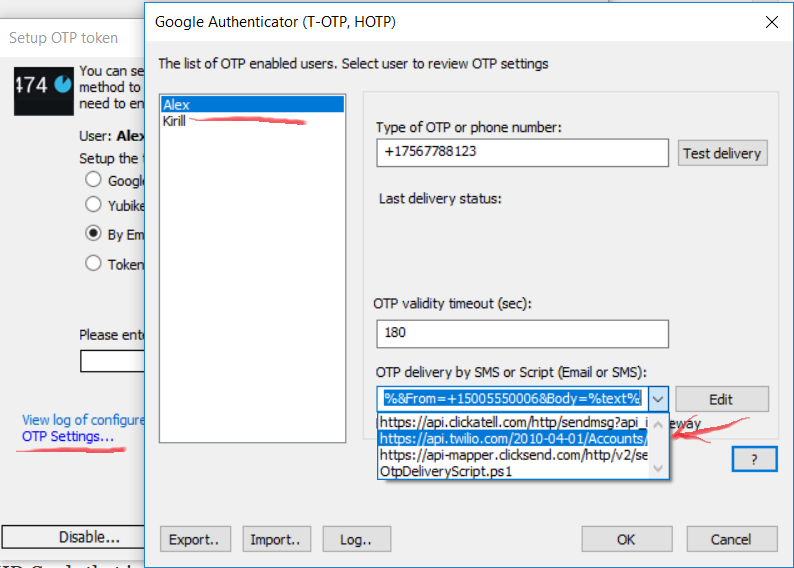
Then you need to open regedit
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Rohos\OtpModule
and add 2 string values:
SMS-Gate-Param = ACxxxxxxxx:token
SMS-Gate-Success-Value = queued
Click Test delivery to ensure it works as expected.
Windows Logon Password replacement with RFID Cards
Rohos Logon Key support the majority models of RFID HID Cards that is used as swipe to enter doors or badge cards. Recently we also have added support of Ironlogic Z2 RFID reader (13,56 MHz и 125 KHz), that is analogue to Elatec TWN3 Multy.
Logon convenience : PIN code and Card. Password and Card. Or complete password replacement with just a Card.
Features :
- Volume Import RFID Cards/tags by UID number. This can be done by using CSV file with the list of users and the card UID per each user.
- Self service support. To finish Card configuration, Users will enter password during first login with a Card on a workstation.
- Password renewal policy support. User needs will provide new password and it will be associated with a Card
- Simple management: Rohos Remote Config allows to easily reset card configuration, block access or replace Card.
- MFA decision support: Single factor authentication or multi factor authentication.
Example CSV File for import:
User1,1000201,-
User2,1000202,-
Where “1000201” is a Card UID. “-” means self service mode, so User will enter password during first login and it will be associated with logon profile stored in Active Directory. After that password replacement is applied.
About Rohos Logon Key software
 Rohos Logon Key adds strong two-factor authentication control for Windows login. Rohos allows to implement multi-factor authentication decision solution, where you can combine different authentication modalities: password, PIN code, regular USB stick, Smartphone or strong authentication devices like U2F key, Yubikey, Google Authenticator one-time password codes, SafeNet iKey tokens or RFID cards. With Rohos you can protect standalone computers , Active Directory workstations and Terminnal Servers as well.
Rohos Logon Key adds strong two-factor authentication control for Windows login. Rohos allows to implement multi-factor authentication decision solution, where you can combine different authentication modalities: password, PIN code, regular USB stick, Smartphone or strong authentication devices like U2F key, Yubikey, Google Authenticator one-time password codes, SafeNet iKey tokens or RFID cards. With Rohos you can protect standalone computers , Active Directory workstations and Terminnal Servers as well.
You can download 15-day trial>
