P2P encryption ownership in secure online storage products (Mega.nz, OneDrive)
Briefly: Secure storage services such as Mega.nz, OneDrive Vault, offers P2P encrypted cloud storage, where the data are being encrypted/ decrypted in your web browser or computer. This provides the highest privacy level since data delivered to the cloud storage in encrypted form. Does it really mean, the information cannot be accessed by the Vendor? Here we show, how the vendor completely owns encryption protocol and data flows, even in your web browser. We also demonstrate why total ownership gives vendors the tools for user targeting that may be used to de-private your data. An example with Rohos Disk cloud folder encryption demonstrates the difference.
P2P Encryption for cloud storage
When you are using such cloud storage as Dropbox, OneDrive, or Google Drive all of your documents may be accessed by a storage vendor for good things such as text search, online image processing, online document editing, etc. Also, it has been noticed that Vendors start developing Machine Learning features that need a huge amount of data to train, so they may take information from your online Files (the Data) and then feed it to the code to derive digital models from your behavior or online habits. These models later may be used to design new features that you may actually need in the near future, but can’t say now about it. So now we definitely can say that Cloud Providers may use your data in an automated way by using a machine. To regulate this issue General Data Protection Rules (GDPR) were developed to allow us (users of cloud storage) to know how our data is being processed and how many 3rd parties are involved.
To address this issue Mega.nz one of the first, offered a new approach called P2P Encrypted cloud storage (Pont-to-Point). Vendor (mega.nz) doesn’t have access to the information stored in your files, since before upload, files being encrypted on your computer (in a Web Browser on-the-fly) by using a secret key that known only to the user. So your Browser is the only Point where decryption and encryption happens.
The following picture demonstrates how the Vendor see your Files uploaded on the server :
P2P Encryption ownership
From the following picture you may see how Storage and Access Point organized with Point-2-Point encryption. Mega.nz provides all parts of service at any given moment of its usage: Storage, Access Point, and Encryption Code. Parts 1, 2 represent Java-Script/HTML code loaded from Mega.nz each time you open mega.nz in a web browser. Parts 3 and 4 represent the most critical part: your data in decrypted form, these parts are being created, accessed, and maintained by parts 1,2 (i.e. Vendor) but they never leave your computer/browser according to the Vendor statement (and source code). The dashed line on the picture below shows the actual ownership area of Mega.nz, as you see items 3,4 are accessed by the Mega.nz at any moment.
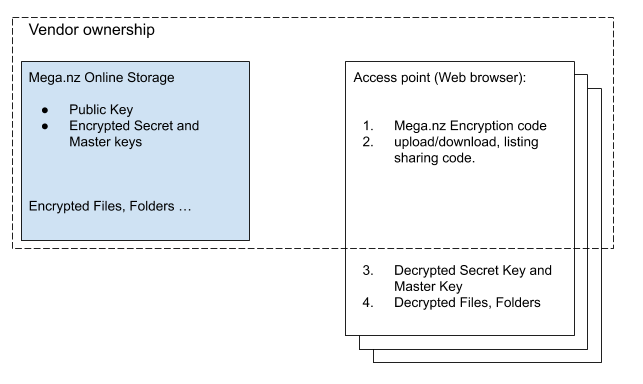
Mega.nz is able to retrieve parts 3,4 from your web browser just with a single update in part 1, when you log in next time. For SaaS vendors (Software as a Service like OneDrive, Mega.nz) it is a built-in feature to be able to target a group of customers by using some criteria (like country, IP, name, email, or other properties derived from complex aggregation algorithms such as behavior, political status, KYC or AML policies) and then deliver them a special software release (encryption code 1) in such a way so that nobody else would know about it. Such targeting is almost impossible to identify. As a result, you as a user start using a “bit different” copy of the product, specially customized and delivered for you, for a special purpose. The same applies to any other product offered by Security as a Service principle LastPass, DUO, etc.
When you use Mega.nz or OneDrive applications on a computer, the ownership area looks the same except that parts 1,2 cannot be quickly changed in a dynamic way as a result of vendor targeting, which is good at some point.
Compare Rohos Disk with Mega.nz
When you use regular cloud storage (as Google Drive) with 3rd party encryption tools like BoxCryptor, VeraCrypt or Rohos Disk Encryption, the ownership areas look different. Opposite to Mega.nz/OneDrive, with a single ownership area of the P2P Encryption process, Rohos provides Encryption Code and an opportunity to have a physical access key with an encryption key on it. When you are using the Rohos Disk app, or its alternatives the entire process does not belong to a single Vendor and thus cannot be targeted by any vendor, with the purpose of identification, de-anonymization, or privacy violation. The following picture illustrates the process when you are using online file storage and offline encryption tools installed on the computer:
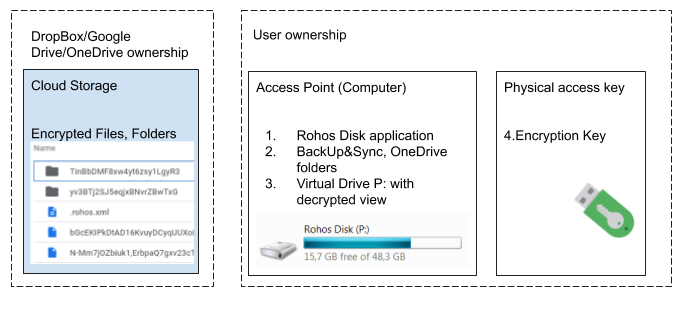
Such tools like Rohos Disk or VeraCrypt are completely on-premise, offline, and classical apps, once downloaded and installed it doesn’t create an online account for your identity, therefore customer tracking and targeting is not possible technically. Learn more how Rohos Disk encrypt the local copy of your Cloud Storage before it will be uploaded to the Internet.
About Rohos Disk Encryption

Rohos Disk program allows you to encrypt your computer, USB flash drive, or cloud storage folders. It is designed for those who have megabytes of sensitive files and who is really concerned with privacy and information security. To protect access to encrypted data you can use electronic keys like USB tokens or RFID smart-cards.
