MFA for Remote Desktop access with U2F FIDO security keys in Rohos Logon Key v.4.7
Rohos Logon Key v.4.7 now has multiple improvements, allows using U2F FIDO security keys as a second authentication factor for Remote Desktop access. This makes Rohos absolutely unique solution that allows using U2F keys for Remote Desktop 2FA login as well as console-based login.
We also added an experimental feature to Rohos Logon to work as a password filler for the LastPass browser extension (experimental).
During pandemic remote access became very popular and sometimes mandatory due to restrictions. Rohos Logon Key allows protecting remote access with convenient two-factor authentication. Rohos may easily work over a classic Microsoft RDP as well as other popular solutions like TeamViewer, AnyDesk, VNC, UltraVNC, MagicConnet , Proxy Networks, LogMeIn, pcAnywhere etc. Currently Rohos Logon Key is the only solution that allows to protect Terminal Server remote access with U2F security keys which is being considered as the strongest authentication factor today.
What’s new in Rohos Logon Key v.4.7 :
- Added a possibility to use U2F FIDO security keys for Windows remote desktop access. RemoteFX device redirection option in MS RDC should be used by Network Admins, to setup U2F keys on TS host side. “Rohos Logon Key compact” setup should be installed on client PC. More details read below.
- Added support of 16/32 bytes HOTP tokens/keys and other minor improvements for One-Time-Password MFA method.
- Added support for Omnikey RFID readers.
- Added support for LastPass automated login with Rohos MFA Key, by inserting a password right to LastPass plugin via web browser extension. Rohos may enter your password right to LastPass login screen in Chrome/Firefox or some website. Current MFA Key is used as password storage. This is an experimental feature for those who prefer to keep LastPass locked after inactivity timeout.
- Minor Improvements in Rohos Logon Key Push token MFA method. Added possibility to setup Smartphone login without entering user account password.
- Added a possibility to enter a specific Username in the “Setup Key” dialog box, which allows to setup a key for users which cannot be resolved with the “Select Users” dialog provided by Windows API.
Improvements with Emergency Logon functionality with an online user account (email address is used). - Improvements with Emergency Logon functionality with online user account (email address is used).
- Added a possibility to display Message Box in RDP login screen, thus populating Remote Access dialog full screen allowing user to enter OTP credentials (by using RDP_notice registry value).
- Fixed issue with “Setup Key” dialog box when user password is empty
- Added a possibility to Add MFA keys with a flag “user must enter password during next MFA login”. That allows to setup keys/cards without entering user account password.
- Rohos Management Tools update.
- Other bug fixing.
How to use U2F FIDO security key for Microsoft Remote Desktop MFA access
Rohos Logon Key allows using FIDO U2F keys to protect Terminal Server with the strongest MFA method.
How to setup Rohos on client PC:
- Download Rohos Logon Key Compact setup file download>>
- Install with command line – rohos_logon_compact.exe /VERYSILENT /usbdev=rohos_u2f.dll
Rohos Logon Key Compact installs a plugin component for MS Remote Desktop Connection application. This component uses RDP Virtual Channels to allow U2F challenge response authentication with Rohos on remote server. This component is required since RemoteFX functionality does not work while Remote Session has Windows Logon screen.
How to setup Rohos Logon Key on Terminal Server:
First, you need to setup RemoteFX device redirection on your Local PC and Terminal Server, use this guide>. As an alternative you may also attach U2F keys directly to Windows Server if your virtualization solution allows it.
- Connect to TS with redirected U2F key.
- Install Rohos Logon Key
- Open Setup Key, and choose U2F Security Key as MFA device type, choose user and click Setup Key.
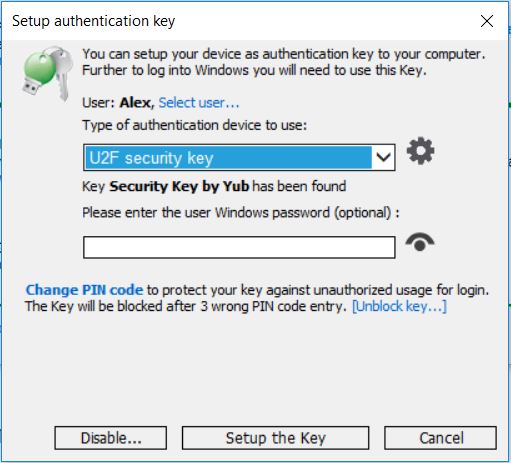
- Open Options and choose MFA policy “For Remote Desktop Users”, setup Emergency Login.
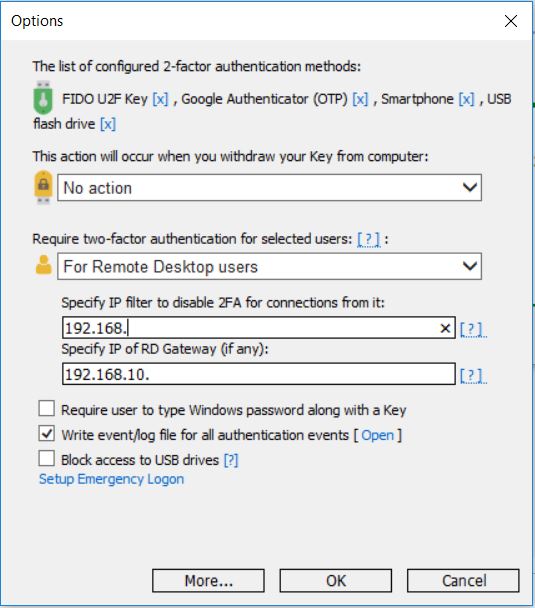
MFA setup is done!
Now you can use U2F Key for MFA login into a previously configured user account. NLA password is used by the underlying authentication system to let you into the Remote Login screen, and then Rohos Logon Key applies 2FA control by performing a Challenge-Response communication with remote U2F key. The remote key provides a unique digital signature as a response, Rohos on the TS side grants or rejects remote desktop access upon verifying the signature.
Download
Download 15-day trial (betta v.4.7) >>
Download Rohos Logon Key compact >>
Download Rohos Management Tools (betta v.4.7) >>
About Rohos Logon Key
 Rohos Logon Key adds strong two-factor authentication control for Windows login. Rohos allows implementing multi-factor authentication decision solution, where you can combine different authentication devices: password, PIN code, regular USB stick, Smartphone or strong authentication devices like U2F key, YubiKey, Google Authenticator one-time password codes, SafeNet iKey tokens or RFID cards. With Rohos you can protect standalone computers, Active Directory workstations or Terminal Servers that works over RDP or other remote assistance solutions like TeamViewer or AnyDesk.
Rohos Logon Key adds strong two-factor authentication control for Windows login. Rohos allows implementing multi-factor authentication decision solution, where you can combine different authentication devices: password, PIN code, regular USB stick, Smartphone or strong authentication devices like U2F key, YubiKey, Google Authenticator one-time password codes, SafeNet iKey tokens or RFID cards. With Rohos you can protect standalone computers, Active Directory workstations or Terminal Servers that works over RDP or other remote assistance solutions like TeamViewer or AnyDesk.
