We’d like to present you the review of Silicon Power F600 FingerPrint Disk with 1Gb volume with on-board fingerprint scanner. It’s not compatible with Rohos Logon Key.

Silicon Power F600 features:
- All flash memory is protected. There is no Open part.
- Biometric or password protection of the USB flash drive (or both, fingerprint + password).
- Compatible with Windows 2000, XP. Doesn’t support Windows Vista (however, there is info on the manufacturer’s web page that 2GB models support Vista)
- There are embedded Programs: File encryption on the disk, Desktop Lock, etc.
- It’s possible to lock/unlock desktop upon USB drive removal (but not full logon as there is in Rohos).
How the device works:
Once the USB drive is plugged in in “My computer†window will appear two devices, removable drive (for example G:\) and virtual CD-ROM (F:\).
Â

If you try to access disk G:\ now it will not open up. It means that it’s locked. To unlock it you should start up the file: “F:\FingerPrint.exeâ€, and in the emerged window choose the icon “Unlockâ€. After this should open up the “fingerprint†authorization window. In this window you may either enter your password or register your fingerprint.

If you have successfully got authorized the disk G:\ will get unlocked, and in the taskbar will appear new icon:

If you double-click on it the program main menu will come up:

From this window you may encrypt the disk back just by pressing the “Unlock†button.
Registering fingerprints:
First you should open the program’s main window and choose the “FP Manager†button. Then enter your name and press the button with the right arrow, and the following window will open up:

Further choose the finger and slide it three times over the scanner, then press right arrow button. In the next window you may set up a password if needed.
“SecretZIP†feature:
In the main menu choose the “SecretZip†button, enroll using fingerprint. The following window will appear:

There are three buttons on the window:
- Create Archive – You choose the files and folders you need, and put them in a usual archive *.zip or encrypted *.exe, that could be unzipped only using this program.
- Unzip the archive – Just choose beforehand created *.zip file and unzip it into a chosen folder.
- Decrypt file – Choose beforehand created encrypted file of *.exe format and the program itself will decrypt it.
Data Synchronization:
In the program’s main menu choose the “Data Synchronization†button, enroll using fingerprint”. The following window will appear:

Â
The left icon will lead to the Settings window, the right one to synchronization window:

There are three buttons (folders) for your disposal. Under each of there there is a button with arrow. If pressing on one of them there will appear the window where you should indicate the path to any folder that is on hard drive and path to the folder from the flash drive for the program to “know” what to synchronize with what. Now you may press the corresponding button (â€syncr. my DataSync folderâ€, “syncr. my favorite folder†or “syncr. my document folderâ€), then press the“Synchronize†button and that’s it.
Locking computer:
In the program’s main menu choose the “PC Lock†button, enroll using fingerprint. The following window will appear:

Here you should set up locking settings and press ОК. Now to lock computer you should unplug the flash drive, and to unlock it to plug the flash drive back. Locking the PC is possible only after the flash drive itself is unlocked.
Summary
- The device doesn’t work under Windows Vista
- On the PC without admin rights the device is not accessible
- Presently it’s not compatible with Rohos Logon Key
- It’s not possible to format the USB flash drive into NTFS format





 The next beta version of Rohos Logon Key includes a feature BlueTooth Wireless Logon that means you can log into Windows computer by using Bluetooth enabled Pocket PC or mobile.
The next beta version of Rohos Logon Key includes a feature BlueTooth Wireless Logon that means you can log into Windows computer by using Bluetooth enabled Pocket PC or mobile.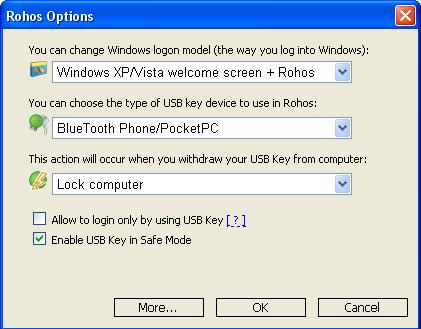

 The new version of Rohos Disk (1.18) includes new utility,
The new version of Rohos Disk (1.18) includes new utility, 
