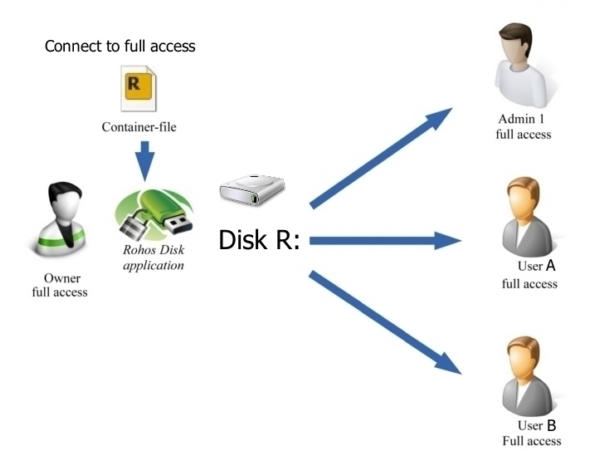
Rohos Disk Encryption allows you to set up shared access to an encrypted disk for various purposes:
- Common access to all users of a single computer.
This is the default behavior of Rohos Disk letter access mode. All users on a computer or terminal server is able to access and work with encrypted drive letter. Users do not need to know the disk password, and they do not need to run the Rohos Disk program. Nobody knows where the disk file container and cannot delete it. The password for accessing the disk is entered by the Administrator or the owner of the Rohos disk.
- Access rules on a Windows Terminal Server.
In this case only selected users knows the password for the disk. Each user enters the password for accessing the disk independently whenever necessary. Secured Disk is accessed by using plain password or a hardware based key.
- Shared access through a shared network folder.
The Rohos disk drive letter will be open for common access on the local network from the computer which acts as the file server. Entering the password to enable the Rohos disk is done by the Administrator or owner of the Rohos disk once per day. He or she will also grant users privileges for network access and is also responsible for making backups and shutting down access to the disk.
Common access for all users of a single computer.
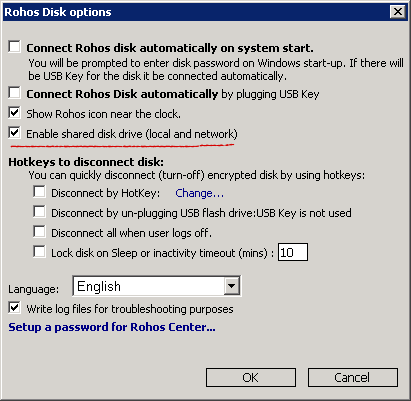
In the Rohos Disk options you must tick the “Enable shared disk drive (local and network)” – this option is ON by default.
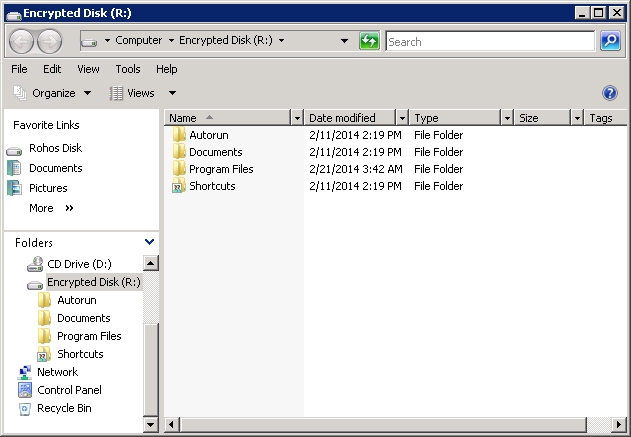
In this case, when one user connects a Rohos disk, the drive letter of this disk will be immediately visible to all users when they open Explorer.
When the read-only option is set, users (including the owner) cannot change the contents of the Rohos disk.
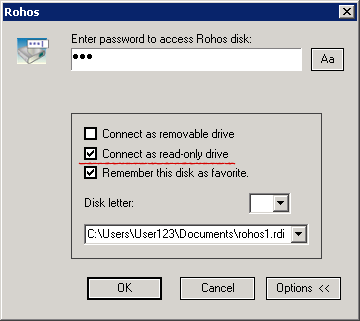
You can set up different rights for reading and writing to the folder within the disk itself. You give some users full control, while other users will have read-only access, and a third group will not be authorized to view the contents of the secret Rohos disk at all.
Advantages of this method:
- Only one user, the owner of the disk, has the password.
- Ability to limit access to certain users.
- The disk can be located in a place where only its owner has access to it, which limits the possibility that it can be copied or deleted by others.
- Users do not need to know the password for the secret disk, and the drive letter will be immediately visible in Explorer.
- This setup is also suitable for users on a Terminal server. Work folders with especially important and confidential files and programs can be converted to a Rohos disk using the “Encrypt folder” function. This will make the disk protection transparent to users of the remote desktop.
Features of this method:
When opening Rohos Disk for other users, the drive letter will be visible among the computer’s additional disks. If it is suddenly turned off, it will become inaccessible for all users. To avoid this, you can deny users the right to launch Rohos Disk on the server by protecting it with a password.
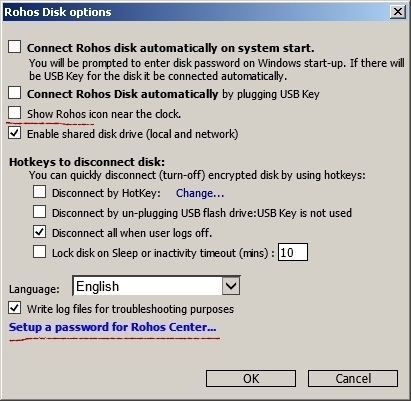
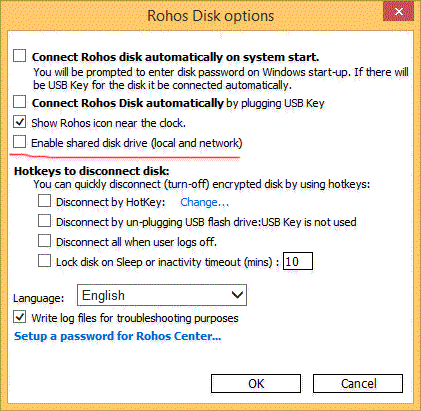
In addition, you must uncheck the option Show Rohos Icon near the clock so that users cannot manage the disk by clicking on the icon near the clock.
Access rules on a Windows Terminal Server.
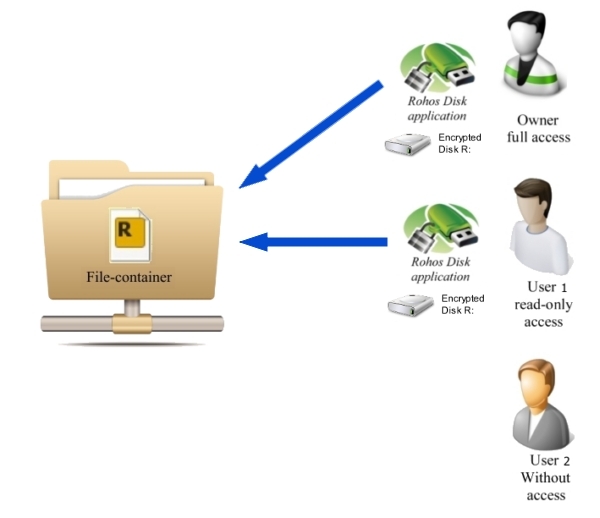
To set up this form of common access:
1. You must turn off the option Enable shared Disk drive. In this case the secret disk letter will be accessible only to a session or user account where the password for this encrypted disk has been entered.

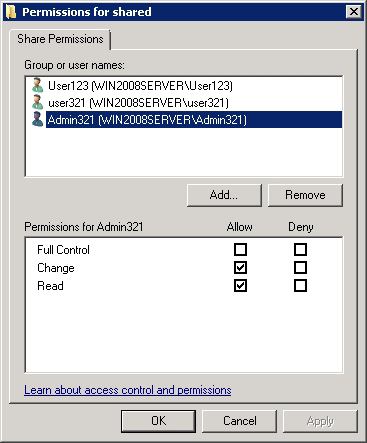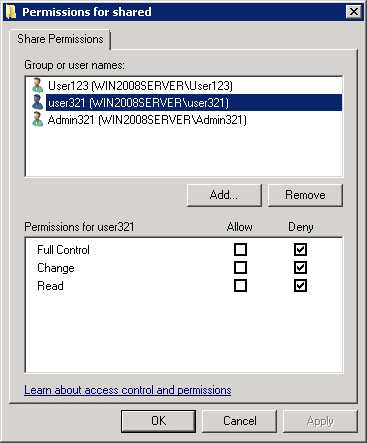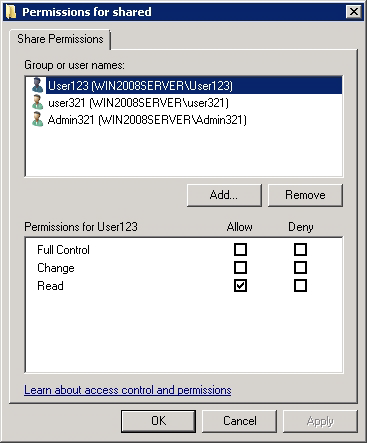
2. The file container should be placed in a common-access folder and different access rights should be granted for different users in order to prevent unauthorized copying or deletion of this file. Some users will be able to open the folder for reading and writing, while other users will have read-only access. Other users still will not be able to view it at all.
3. It is necessary to create a shortcut for accessing this disk and copy it onto the desktop of the selected users. To do this, in the main window go to Rohos Disk Encryption > Disk > Tools > Create disk shortcut. Then a file with the given shortcut will be visible on the desktop.
4. You can give the password for the Rohos disk to all users or hand out access keys such SafeNet ikey, eToken or any other PKCS#11-compatible.
Advantages of this method:
- Only a selected group of users will be able to access Encrypted Disk letter.
- The secret drive letter will be protected from other terminal sessions.
- By using hardware USB token you protect the disk password from being revealed on a thin client side.
- Open source and strong AES-256 bit encryption by using open and NIST approved data security standards.
Shared access through a shared network folder
The entire Rohos encrypted disk or some folders on it can be opened up for common access over the network. Select the disk in My Computer and enter its properties through the context menu.
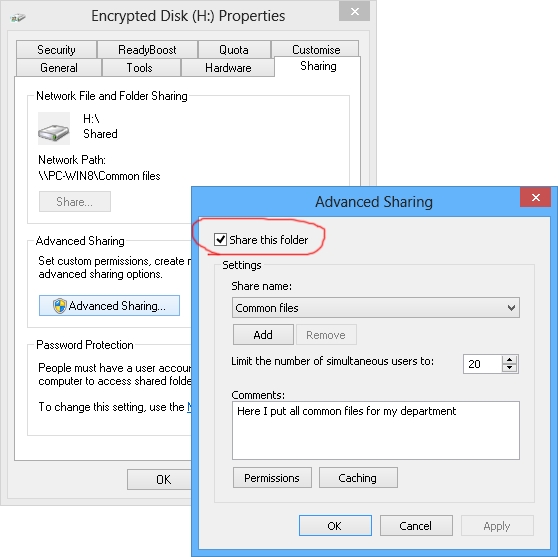
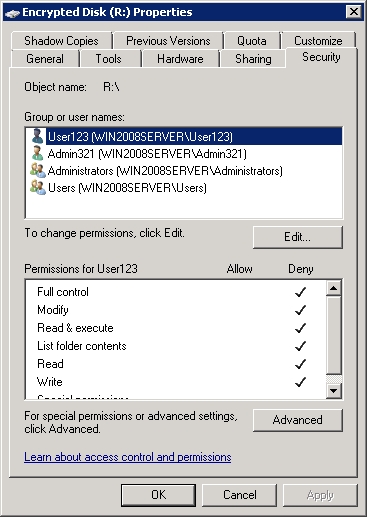
Assigning access to this disk for different categories of network users can be done here with the Permissions command.
Connect the Rohos disk network folder to the workstations on the network:
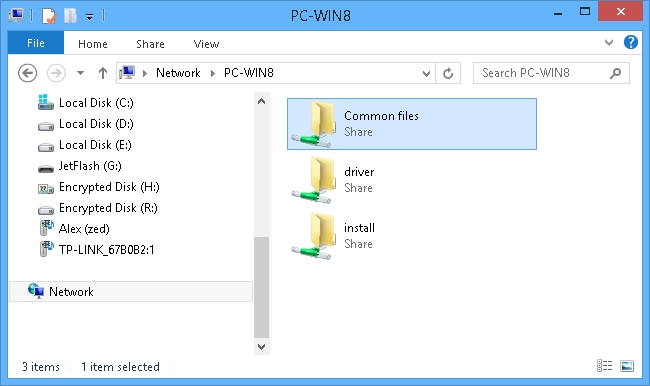
Advantages of this way of assigning access:
- The encrypted disk can be located on both on a computer or a connected USB storage device.
- You set it up so that when a USB storage device is disconnected, the encrypted disk will be automatically disabled, the network folder will disappear, and it will no longer be possible to access it.
- You can set up a hardware security module (HSM) for accessing the secret disk, e.g. USB tokens like ruToken, iKey, or eToken. You can entrust such a token for the disk to the employee responsible for activating the disk. When the token is disconnected from the PC, the disk will automatically turn off.
- Activating a secret disk can only be done by means of a password or automatically by connecting a USB token.
- Network users do not necessarily have to know the password for the disk to begin working with all, but all data will be reliably secured on the file server.
While one network user is working with one file or directory, another user can work with another file or directory. It will appear as a simple common-access resource. However, as soon as you leave the system, access to it will automatically end.














 In short: now the popular ruToken identification device can be used in Rohos Logon Key and Rohos Disk as the one key needed to log in to Windows and your protected data. Rohos Logon Key works fully on Windows Vista/7 and also supports authorization for remote desktops using a ruToken. User authentication and identification with USB keys.
In short: now the popular ruToken identification device can be used in Rohos Logon Key and Rohos Disk as the one key needed to log in to Windows and your protected data. Rohos Logon Key works fully on Windows Vista/7 and also supports authorization for remote desktops using a ruToken. User authentication and identification with USB keys. We are welcome you to try Rohos Logon Key and Rohos Disk Encryption software on a new amazing operating system released by Microsoft recently.
We are welcome you to try Rohos Logon Key and Rohos Disk Encryption software on a new amazing operating system released by Microsoft recently.