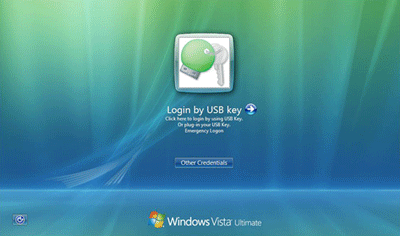
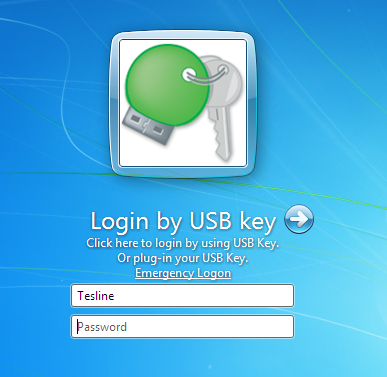
Authentication in Windows/Mac with BlueTooth device
The Rohos Logon Key enables to use wireless devices equipped with Bluetooth for computer security (login, authentication, lock/unlock). Your mobile phone or pocket PC, Palm, Nokia plays the role of your access key from your PC or Mac:
- Automatic Windows/Mac logon when a user approaches the computer (with the mobile phone).
- Computer will be protected with a password, but you don’t have to enter it manually.
Rohos Logon Key is a genuine authentication solution with complete password replacement, and not just a primitive PC locker like many other programs where you have to enter a password manually anyway for logon.
A version for Mac OS X is available also.
How it works:
-
A Computer or Notebook should have a Bluetooth adapter.
- The Rohos Logon saves your phone ID in a wireless way (Bluetooth Mac address).
- When the phone is near your computer, access to it is open: automatic logon or it gets unlocked.
- Also, if you step away from the computer, it will automatically be locked within 5-10 seconds.
* You shouldn’t install additional programs onto your mobile phone or Pocket PC.
How to set up mobile or Pocket PC login:
First step:
- First, you should install the Rohos Logon Key (Windows) or Rohos Logon Key for Mac.
- In the main window screen open dialog box “Options” (or ‘Preferences’ for Mac).
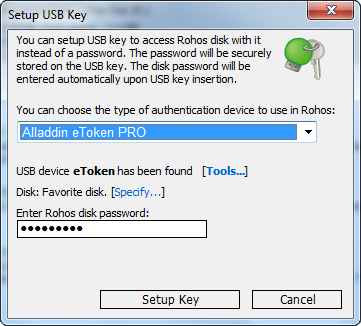
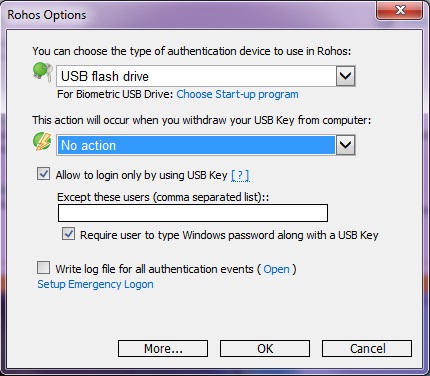
- In this dialog box for the type of device used as a USB key choose Bluetooth Phone/Pocket PC.

Rohos preferences in Mac OS X:
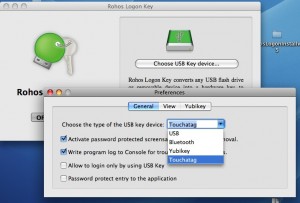
Second step (Windows):
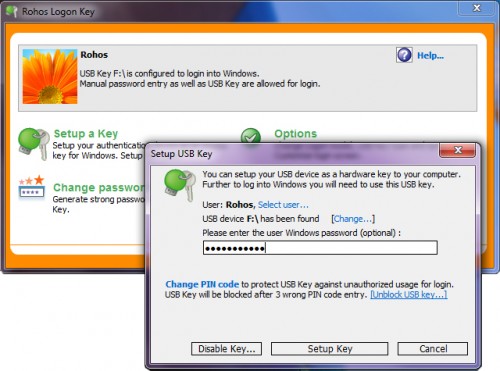
- In the main Rohos window click “Set up USB flash drive”. In the dialog box should appear the name of the Bluetooth device, that was detected within the radius of coverage. (For the device to be detected by other devices you should turn on mobile or Pocket PC Bluetooth feature).
- Please wait up to 30 sec till Rohos Logon detects your mobile device
- Rohos Logon may show dialog box with multiple Bluetooth devices list, please select yours device and click OK.
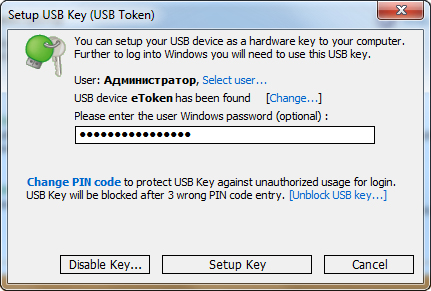
- In the dialog box enter your Windows login password (if you do not use any password, create one) and click ‘Create USB Key’.
- Now you can restart computer
Second step for Mac:
- Click “Choose your USB Key device” button, wait till your Bluetooth device appears in the list and click OK.
- Enter your Mac OS X password
Restart or log off Windows/Mac, please wait 5-10 seconds. Rohos Logon Key will detect mobile phone within the radius of coverage and will automatically log on.
Bluetooth Logon Security:
This software solution is safe from the point of view of computer security:
- Rohos Logon Key doesn’t save any passwords either on a phone or on Pocket PC.
- Your logon password is saved on the local computer in encrypted form.
- The program saves your mobile phone unique identity (Mac address), that is impossible to falsify.
- If you left your phone at home you might use the usual password or emergency logon (that’s offered by Rohos Logon).

Bluetooth operating radius
Bluetooth operating radius may be up to 150 meters. Thus, auto-lock may work not as fast as a user would like it to.
How fast does it lock and unlock Windows
Rohos Logon may detect when the Bluetooth device is within visibility range very quickly, so Windows unlock by Bluetooth may take up to 9 seconds.
Vice versa ‘Bluetooth device is away’ detection works slowly. It can take up to 40 seconds to lock your Windows when the phone is out of the range. It is due to prevent false Desktop locks by the program, because sometimes Bluetooth hardware looses connection for seconds. And Rohos Logon always waits for an extra time to ensure the mobile is away.
How to set a longer time-out to lock the computer when Bluetooth device is away
If you don’t want Rohos Logon to lock you desktop each time you step away from your PC just for a moment you can set up a bigger timeout.
Open regedit.exe go to HKEY_LOCAL_MACHINE \ SOFTWARE \ Rohos
and change USB_Key_remove_behaviour to “60” .
60 means that when Bluetooth device is away after 60 seconds Rohos Logon will lock the desktop (minimum value is 35 seconds).
Known issues
- Bluetooth adapter is installed, but the programs doesn’t detect your phone please, make sure Bluetooth adapter is compatible with Windows and there is Bluetooth blue icon near system clock. Please note: while in all the Rohos dialog boxes is used the term ‘USB flash drive’, it is presupposed to be your Mobile Telephone Bluetooth. This appears to be so because initially the Rohos Logon Software supported only USB flash drives as a USB Key for PC access. The range of the software compatible devices is wider now.
- Rohos Logon does not lock the desktop when I turn-OFF Bluetooth on my phone or step far away for a long time. – Make sure you set a removal behavior in Rohos Options (Lock the desktop upon USB Key removal).
– Make sure you previously log in or unlock your desktop by using Rohos Logon + Bluetooth mobile. Each time you unlock Windows by a password stops Rohos Logon tracking the mobile radio.
– Make sure your set up your mobile phone exactly but not anyone else in the range of visibility. On the Setup USB Key Dialog box you can see your phone name. If it is not your phone name click “choose”and select your phone. - Rohos Logon Key logs into Windows automatically even if my phone away.
– Open the program and click ‘Setup USB Key’ dialog box. If the program anyway detects your mobile (that is away or OFF at the moment) it means there is another technical issue, please contact us. - I use iPhone 3G, iPhone 3GS or iPhone 4 but the desktop is locked immediately after login
– Please note iPhone iOS automatically disables Bluetooth radio if there is no program that use it. - I use wireless keyboard and mouse, and can not log in with Bluetooth and my phone.
– Sometimes two Bluetooth adapters can not work along. So, either keyboard and mouse, or other BT adapter will not work. Select another type of USB key.
System Requirements:
Hardware:
- Any Laptop with Bluetooth hardware or desktop PC + Bluetooth dongle. (Read notes about Toshiba notebooks)
- Any Mobile device with Bluetooth feature, such as mobile phone or PDA.
Operating Systems:
- Any Windows (x32;x64)
- Mac OS X 10.4, 10.5, 10.6 (Rohos Logon Key for Mac).
Bluetooth Driver:
- Microsoft Bluetooth stack drivers – works perfectly.
- WidComm Bluetooth stack- works perfectly.
- BlueSoleil Bluetooth stack drivers – works not so well. Depends on the version.
- Toshiba Bluetooth stack – Used on almost all Toshiba notebooks. It’s almost impossible to use it for logon due to API design. Please search for a solution to reinstall WidComm Bluetooth stack over.
Compatibility status:
Rohos Logon Key for Windows was tested on Laptop models: Acer Aspire, Lenovo, Samsung. And the Mac version was tested on Apple PowerBook G4, MacBook and MacBook Pro models.





 Chisinau, Moldova, December 25, 2009 Tesline-Service SRL, Moldova software company specializing in PC security solutions today announced that it released Rohos Disk Encryption 1.7., with long time anticipated portable data encryption solution for Windows that gives possibility to work with encrypted data in full on any computer without Admin rights.
Chisinau, Moldova, December 25, 2009 Tesline-Service SRL, Moldova software company specializing in PC security solutions today announced that it released Rohos Disk Encryption 1.7., with long time anticipated portable data encryption solution for Windows that gives possibility to work with encrypted data in full on any computer without Admin rights.
 Chisinau, Moldova, March 11, 2009 Tesline-Service SRL, Chisinau, Moldova today announced the release of its new biometric Windows PC authentication solution, Rohos Face Logon.
Chisinau, Moldova, March 11, 2009 Tesline-Service SRL, Chisinau, Moldova today announced the release of its new biometric Windows PC authentication solution, Rohos Face Logon.
 Chisinau, Moldova, November 04, 2008 Tesline-Service SRL, is a small software company specializing in PC security solutions today announced that it’s Rohos Logon Key Mac OS X version – authentication solution for Mac OS X Tiger and Mac OS X Leopard now supports YubiKey.
Chisinau, Moldova, November 04, 2008 Tesline-Service SRL, is a small software company specializing in PC security solutions today announced that it’s Rohos Logon Key Mac OS X version – authentication solution for Mac OS X Tiger and Mac OS X Leopard now supports YubiKey.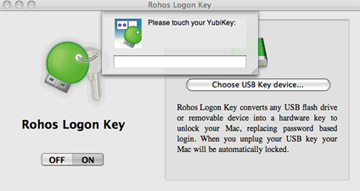

 Chisinau, March 26, 2008 Tesline-Service SRL, is a small software company specializing in PC security solutions today announced that it released Rohos Logon Key 2.5., two-factor authentication solution, whichWorks with Windows Vista.
Chisinau, March 26, 2008 Tesline-Service SRL, is a small software company specializing in PC security solutions today announced that it released Rohos Logon Key 2.5., two-factor authentication solution, whichWorks with Windows Vista.