P2P encryption ownership in secure online storage products (Mega.nz, OneDrive)
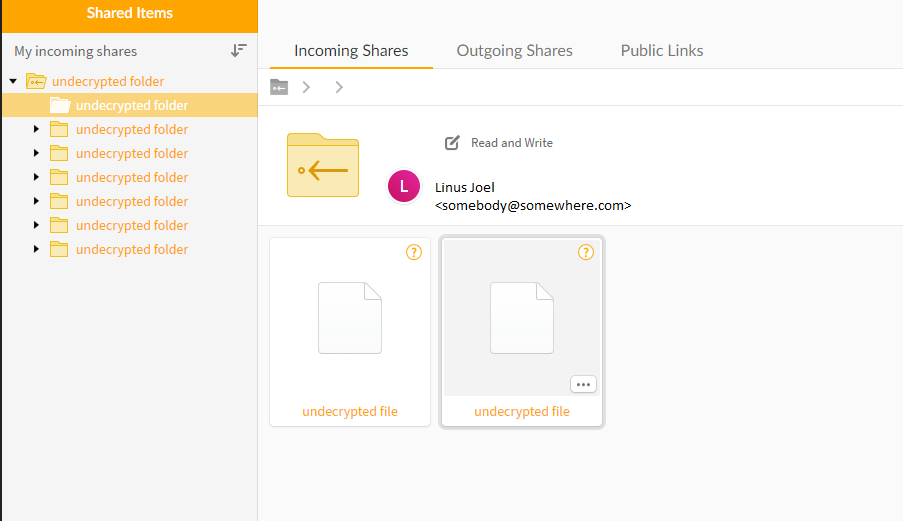
Briefly: Secure storage services such as Mega.nz, OneDrive Vault, offers P2P encrypted cloud storage, where the data are being encrypted/ decrypted in your web browser or computer. This provides the highest privacy level since data delivered to the cloud storage in encrypted form. Does it really mean, the information cannot be accessed by the Vendor? Here we show, how the vendor completely owns encryption protocol and data flows, even in your web browser. We also demonstrate why total ownership gives vendors the tools for user targeting that may be used to de-private your data. An example with Rohos Disk cloud folder encryption demonstrates the difference.
Read more
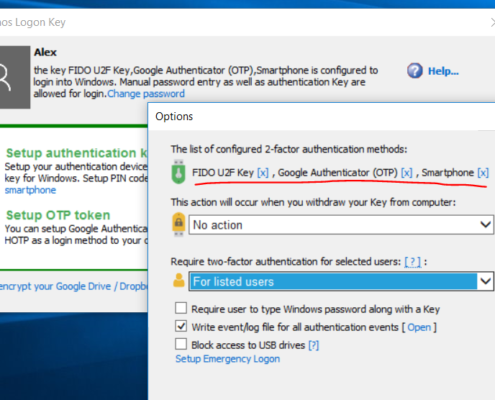
 We are glad to report that Rohos Logon Key for Mac (v3.7) is compatible with macOS Catalina 10.15.2. We have added dark mode support and ensured authentication functionality for USB drive, YubiKey and Bluetooth devices as a key. Due to a few issues we make this release absolutely free.
We are glad to report that Rohos Logon Key for Mac (v3.7) is compatible with macOS Catalina 10.15.2. We have added dark mode support and ensured authentication functionality for USB drive, YubiKey and Bluetooth devices as a key. Due to a few issues we make this release absolutely free.
 We have updated Rohos Management Tools v.4.4 adds improvements and bug fixing for Rohos Logon Key v.4.4 in Active Directory network. New Rohos Management Tools allows better MFA management over Active Directory workstations in isolated environments. With Rohos you can use industry accepted RFID cards such as EM, HID Prox, HiTag, Legic, Mifare as a second/single factor logon method for workstation/HMI terminals.
We have updated Rohos Management Tools v.4.4 adds improvements and bug fixing for Rohos Logon Key v.4.4 in Active Directory network. New Rohos Management Tools allows better MFA management over Active Directory workstations in isolated environments. With Rohos you can use industry accepted RFID cards such as EM, HID Prox, HiTag, Legic, Mifare as a second/single factor logon method for workstation/HMI terminals. We are glad to announce new update for Rohos Face Logon that allows to set adaptivity level for face recognition. This allows quicker login in any lighting conditions.
We are glad to announce new update for Rohos Face Logon that allows to set adaptivity level for face recognition. This allows quicker login in any lighting conditions. We have published Rohos Disk Encryption v.2.7 with new experimental functionality “Encrypt Folder”. This feature that allows to encrypt your Cloud Storage folders like OneDrive, Google Drive and others. Now Rohos is able to encrypt arbitrary files on a computer and thus Cloud Synchronization and Backup tools uploads fully encrypted data to the cloud since the sensitive data appeared on the computer.
We have published Rohos Disk Encryption v.2.7 with new experimental functionality “Encrypt Folder”. This feature that allows to encrypt your Cloud Storage folders like OneDrive, Google Drive and others. Now Rohos is able to encrypt arbitrary files on a computer and thus Cloud Synchronization and Backup tools uploads fully encrypted data to the cloud since the sensitive data appeared on the computer.