Rohos Logon Key v.4.7 now has multiple improvements, allows using U2F FIDO security keys as a second authentication factor for Remote Desktop access. This makes Rohos absolutely unique solution that allows using U2F keys for Remote Desktop 2FA login as well as console-based login.
We also added an experimental feature to Rohos Logon to work as a password filler for the LastPass browser extension (experimental).
During pandemic remote access became very popular and sometimes mandatory due to restrictions. Rohos Logon Key allows protecting remote access with convenient two-factor authentication. Rohos may easily work over a classic Microsoft RDP as well as other popular solutions like TeamViewer, AnyDesk, VNC, UltraVNC, MagicConnet , Proxy Networks, LogMeIn, pcAnywhere etc. Currently Rohos Logon Key is the only solution that allows to protect Terminal Server remote access with U2F security keys which is being considered as the strongest authentication factor today.
What’s new in Rohos Logon Key v.4.7 :
- Added a possibility to use U2F FIDO security keys for Windows remote desktop access. RemoteFX device redirection option in MS RDC should be used by Network Admins, to setup U2F keys on TS host side. “Rohos Logon Key compact” setup should be installed on client PC. More details read below.
- Added support of 16/32 bytes HOTP tokens/keys and other minor improvements for One-Time-Password MFA method.
- Added support for Omnikey RFID readers.
- Added support for LastPass automated login with Rohos MFA Key, by inserting a password right to LastPass plugin via web browser extension. Rohos may enter your password right to LastPass login screen in Chrome/Firefox or some website. Current MFA Key is used as password storage. This is an experimental feature for those who prefer to keep LastPass locked after inactivity timeout.
- Minor Improvements in Rohos Logon Key Push token MFA method. Added possibility to setup Smartphone login without entering user account password.
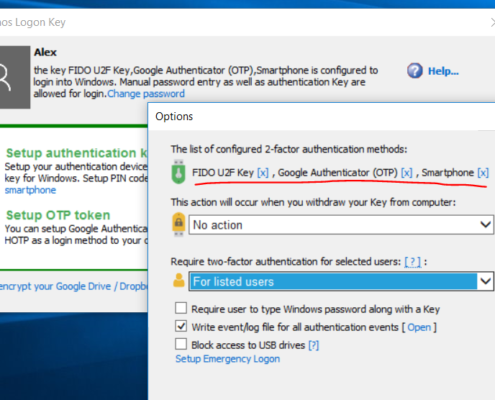
- Added a possibility to enter a specific Username in the “Setup Key” dialog box, which allows to setup a key for users which cannot be resolved with the “Select Users” dialog provided by Windows API.
Improvements with Emergency Logon functionality with an online user account (email address is used).
- Improvements with Emergency Logon functionality with online user account (email address is used).
- Added a possibility to display Message Box in RDP login screen, thus populating Remote Access dialog full screen allowing user to enter OTP credentials (by using RDP_notice registry value).
- Fixed issue with “Setup Key” dialog box when user password is empty
- Added a possibility to Add MFA keys with a flag “user must enter password during next MFA login”. That allows to setup keys/cards without entering user account password.
- Rohos Management Tools update.
- Other bug fixing.
Read more 


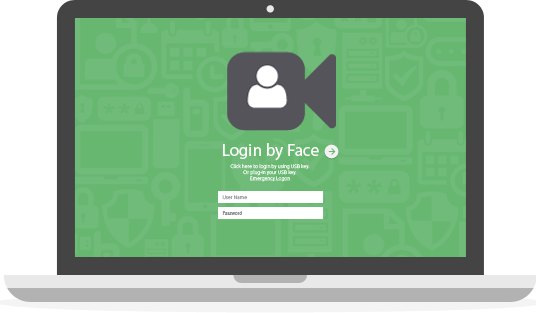 We are glad to announce new update for Rohos Face Logon that allows to set adaptivity level for face recognition. This allows quicker login in any lighting conditions.
We are glad to announce new update for Rohos Face Logon that allows to set adaptivity level for face recognition. This allows quicker login in any lighting conditions. We have published Rohos Disk Encryption v.2.7 with new experimental functionality “Encrypt Folder”. This feature that allows to encrypt your Cloud Storage folders like OneDrive, Google Drive and others. Now Rohos is able to encrypt arbitrary files on a computer and thus Cloud Synchronization and Backup tools uploads fully encrypted data to the cloud since the sensitive data appeared on the computer.
We have published Rohos Disk Encryption v.2.7 with new experimental functionality “Encrypt Folder”. This feature that allows to encrypt your Cloud Storage folders like OneDrive, Google Drive and others. Now Rohos is able to encrypt arbitrary files on a computer and thus Cloud Synchronization and Backup tools uploads fully encrypted data to the cloud since the sensitive data appeared on the computer. Now you can use popular U2F FIDO security keys for Windows logon. Both multi-factor and single-factor authentication use cases are supported as well. It means you can use your U2F key as a password replacement or you can setup true multi-factor authentication to unlock your dektop: U2F Key + your Windows password.
Now you can use popular U2F FIDO security keys for Windows logon. Both multi-factor and single-factor authentication use cases are supported as well. It means you can use your U2F key as a password replacement or you can setup true multi-factor authentication to unlock your dektop: U2F Key + your Windows password.